Continuous Monitoring Plan Template
Continuous Monitoring Plan Template - Start with looking at the specific. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a. Score the judgments • report: Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. Web this guideline helps organizations develop and implement a continuous monitoring program for their information systems and security controls. Web in doing so, it is important that a system’s security architecture, as outlined within the system security plan and supported by the cyber security incident response plan and. Web • plan the approach • conduct: Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system. Web ociso will implement continuous monitoring of systems using continuous diagnostics and mitigation (cdm) and other enterprise security tools as described in. Ongoing information security, vulnerabilities, and threats to. Web in doing so, it is important that a system’s security architecture, as outlined within the system security plan and supported by the cyber security incident response plan and. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. Evaluate the elements. Score the judgments • report: Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s. Ongoing information security, vulnerabilities, and threats to. The purpose of this guideline is to assist organizations in the development of a. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. Web this publication describes an approach for the development of information security continuous monitoring (iscm) program assessment that can be used to evaluate. Web • plan the approach • conduct: Evaluate the elements • conduct: Formulate actions part of. Web • plan the approach • conduct: Start with looking at the specific. Evaluate the elements • conduct: Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system. Web information system continuous monitoring (iscm) plan. Web this document provides guidance on continuous monitoring (conmon) and ongoing authorization in support of maintaining a security authorization that meets the federal. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a. Web information system continuous monitoring (iscm) plan. Web the monitoring plan establishes the guidelines for. Web ociso will implement continuous monitoring of systems using continuous diagnostics and mitigation (cdm) and other enterprise security tools as described in. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. Web • plan the approach • conduct: Formulate actions part of the “plan. The purpose of this. Web in doing so, it is important that a system’s security architecture, as outlined within the system security plan and supported by the cyber security incident response plan and. Web • plan the approach • conduct: Web ociso will implement continuous monitoring of systems using continuous diagnostics and mitigation (cdm) and other enterprise security tools as described in. Start with. Web this document provides guidance on continuous monitoring (conmon) and ongoing authorization in support of maintaining a security authorization that meets the federal. Web • plan the approach • conduct: Evaluate the elements • conduct: Web ociso will implement continuous monitoring of systems using continuous diagnostics and mitigation (cdm) and other enterprise security tools as described in. Web information security. Web • plan the approach • conduct: Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system. Web this publication describes an example methodology for assessing an organization’s information security continuous monitoring (iscm) program. The purpose of this guideline is to assist organizations in. Web in doing so, it is important that a system’s security architecture, as outlined within the system security plan and supported by the cyber security incident response plan and. Web this document provides guidance on continuous monitoring (conmon) and ongoing authorization in support of maintaining a security authorization that meets the federal. The purpose of this guideline is to assist. Web this publication describes an approach for the development of information security continuous monitoring (iscm) program assessment that can be used to evaluate. Web as defined by the national institute of standards and technology (nist), the process for continuous monitoring includes the following initiatives: Web this document provides guidance on continuous monitoring (conmon) and ongoing authorization in support of maintaining a security authorization that meets the federal. Web in doing so, it is important that a system’s security architecture, as outlined within the system security plan and supported by the cyber security incident response plan and. Ongoing information security, vulnerabilities, and threats to. Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system. Web this guideline helps organizations develop and implement a continuous monitoring program for their information systems and security controls. Formulate actions part of the “plan. Web information system continuous monitoring (iscm) plan. Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. Score the judgments • report: Start with looking at the specific. Web • plan the approach • conduct: Web ociso will implement continuous monitoring of systems using continuous diagnostics and mitigation (cdm) and other enterprise security tools as described in.
Continuous Monitoring Plan Template
Monitoring Chart Templates at

5s Manufacturing Assessment Lean Six Sigma Templates Qualads
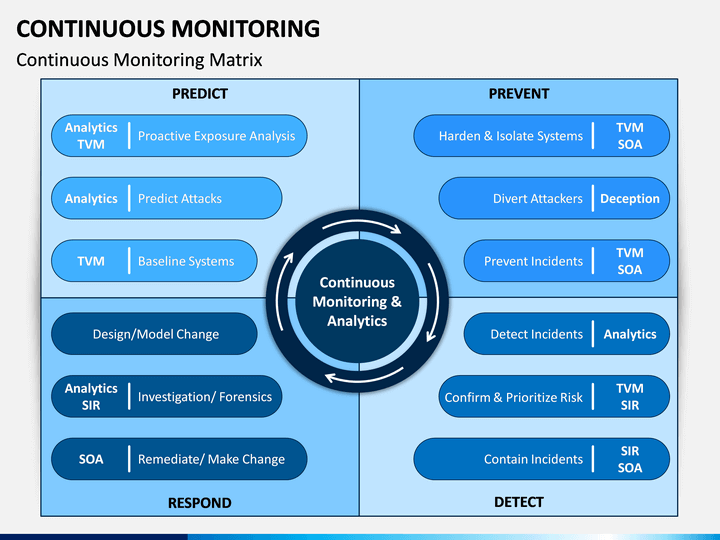
Continuous Monitoring PowerPoint Template
Continuous Monitoring Plan Template
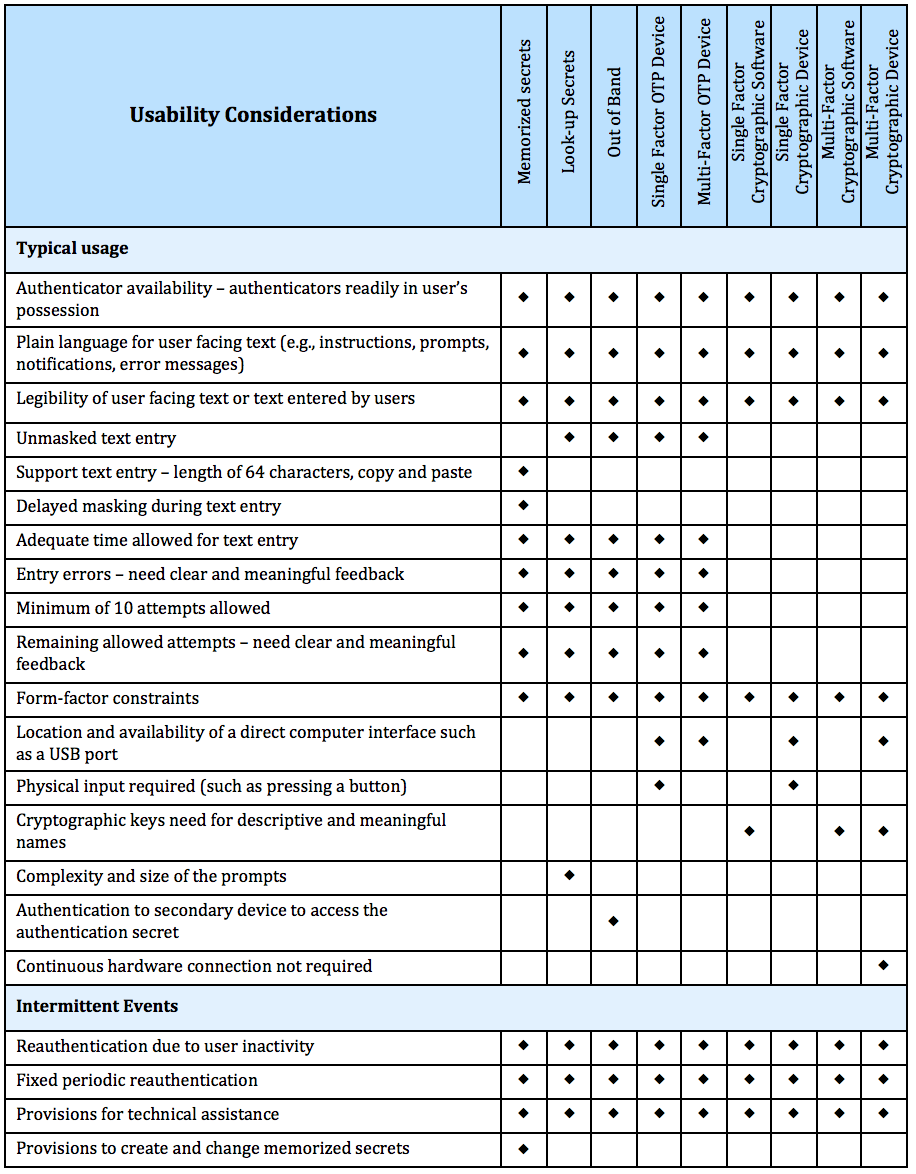
Rmf Continuous Monitoring Plan Template
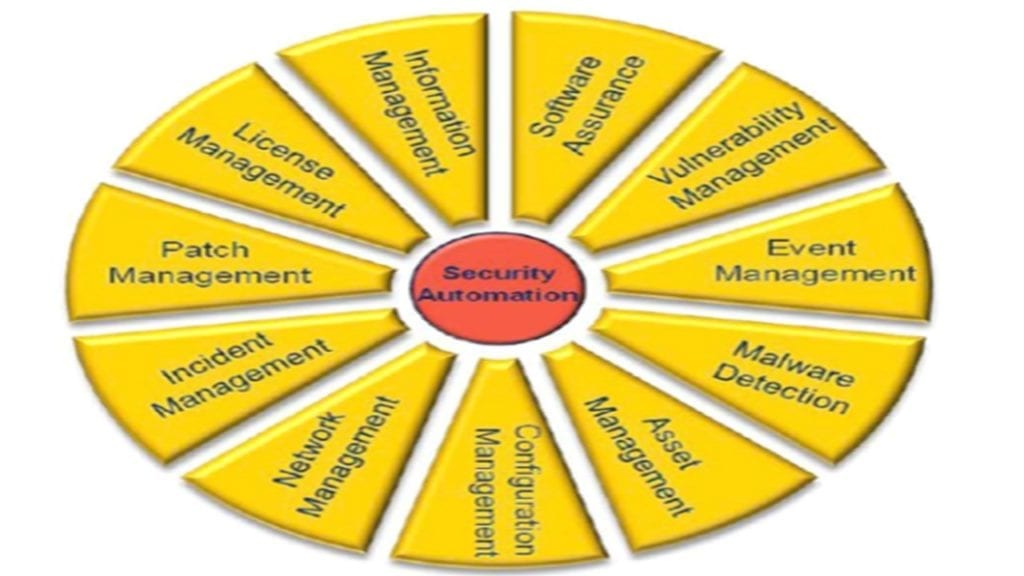
TEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
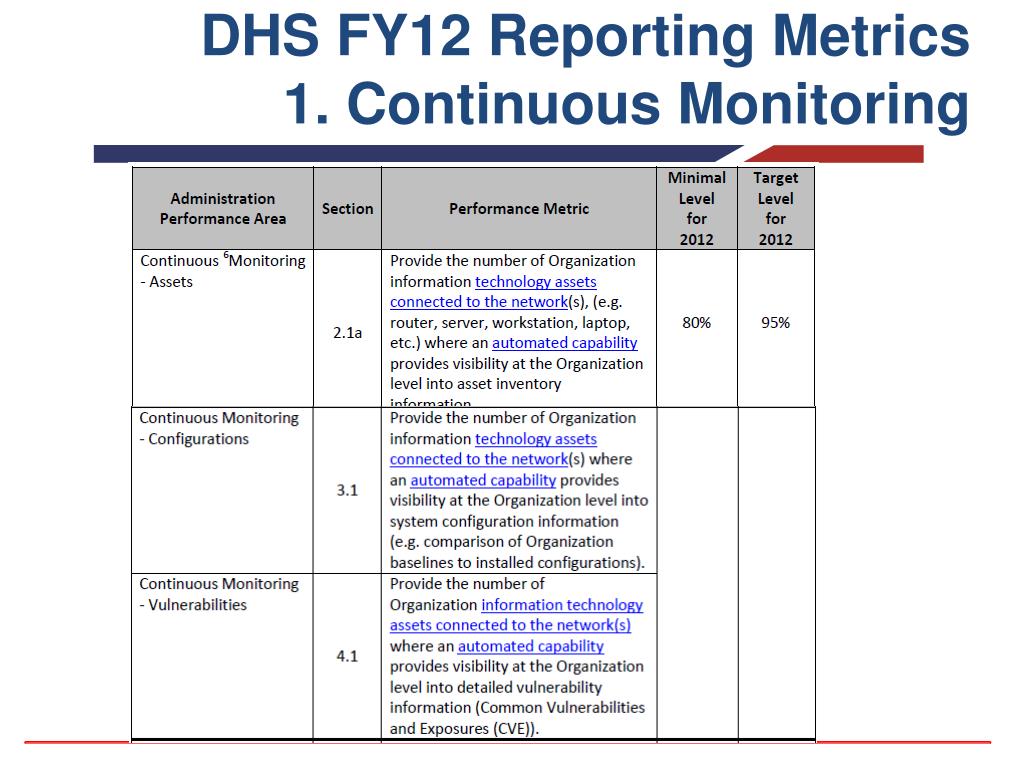
Continuous Monitoring Plan Template
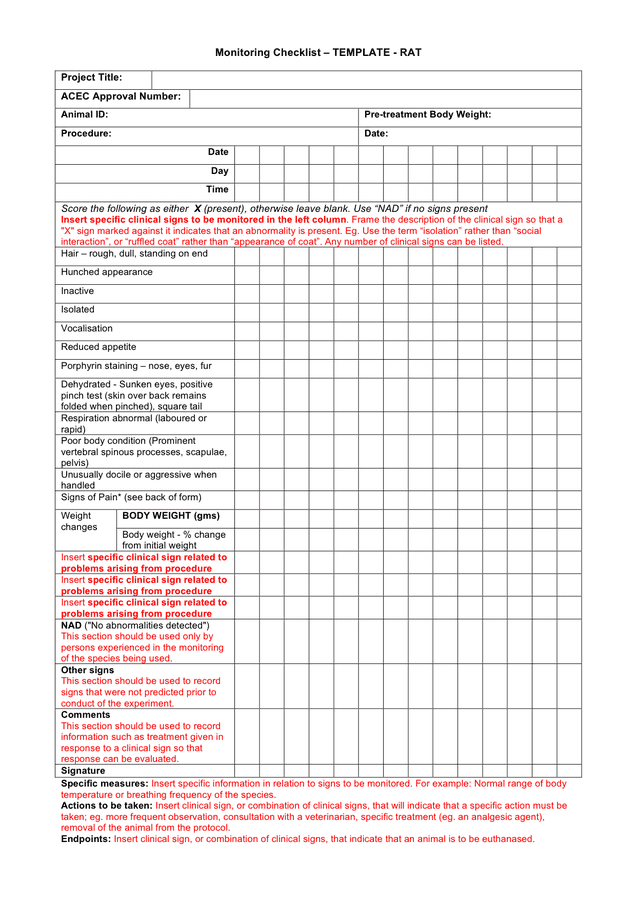
Monitoring checklist template in Word and Pdf formats
.png?auto=compress,format)
6 Benefits of Continuous Monitoring for Cybersecurity
Web Nistir 8212, An Information Security Continuous Monitoring Program Assessment, Provides An Operational Approach To The Assessment Of An Organization’s.
Evaluate The Elements • Conduct:
Web The Monitoring Plan Establishes The Guidelines For Conducting Monitoring Visits And Related Tasks For Monitoring The Survey Protocol [Reference Protocol Number And Title].
Web This Publication Describes An Example Methodology For Assessing An Organization’s Information Security Continuous Monitoring (Iscm) Program.
Related Post: