Cyber Security Incident Response Plan Template
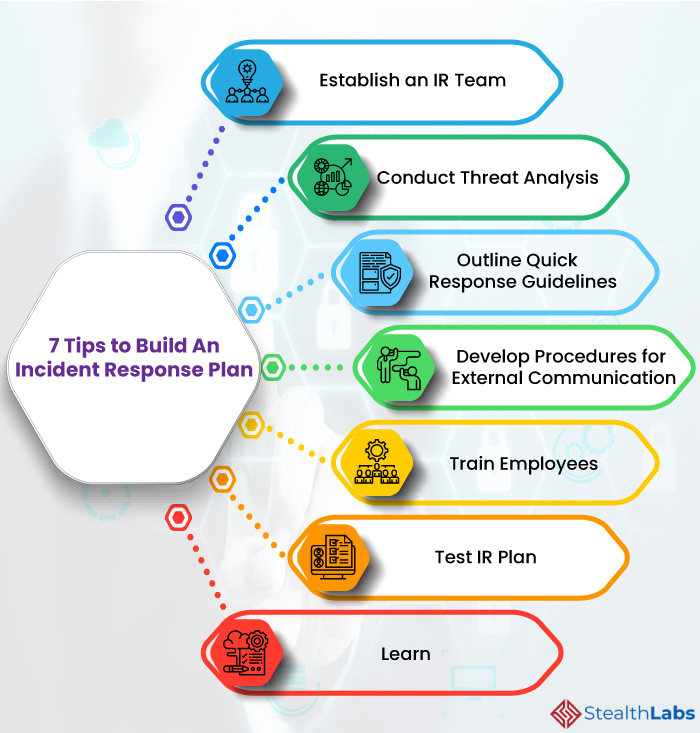
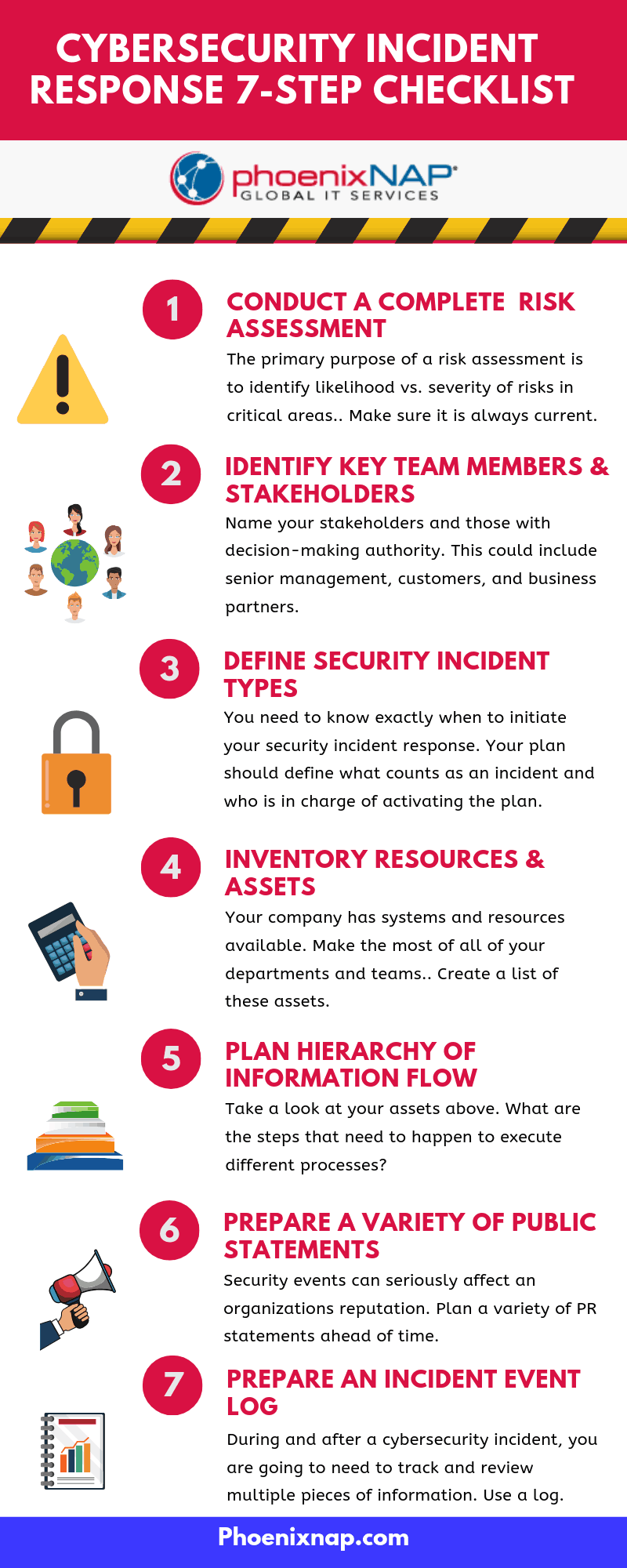
Cyber Security Incident Response Plan Template - Web the most important steps to take in the wake of a cyber attacks. Web cyber security incident response (ir) is a set of information security policies and procedures used to prepare, detect, contain and recover data from any breach. Web 5 best practices for building a cyber incident response plan; Without a detailed irp, organizations risk prolonged downtime, data loss, and significant financial and reputational damage. An incident response plan template can help organizations outline exact instructions that detect, respond to and limit the effects of security incidents. It involves installing the security solution in software, hardware, and other technologies in the system. How incident response supports the organization’s broader mission. At a minimum, an incident response plan should be reviewed & updated at least once every three years. Incident response planning often includes the following details: It should also include a cybersecurity list of key. Web 5 best practices for building a cyber incident response plan; This segment is sponsored by graylog. Web tips on how to write a cybersecurity incident response plan. Testing frequency is at an organization's discretion. Web testing & review cycle. Web an incident response plan provides a systematic approach to managing the aftermath of a security breach or cyber attack. Plan and coordinate a rapid response. Computer security incident response has become a critical business activity today, given the growing complexity and number of cyber attacks, ransomware attacks and data breaches across the globe. It aims to handle the situation. The organization’s approach to incident response. The template helps enable your it operations, security, and incident response teams to: Web regardless of the incident scope, your goal is to be able to perform the necessary steps and take into account any unexpected contingencies. Web what is a security incident response plan? It should also include a cybersecurity list of key. It aims to handle the situation in a way that limits damage and reduces recovery time and costs. Web tips on how to write a cybersecurity incident response plan. Web nist incident response plan. Computer security incident response has become a critical business activity today, given the growing complexity and number of cyber attacks, ransomware attacks and data breaches across. Web delinea’s free cybersecurity incident response plan template helps you reduce the risk of a cyber breach becoming a catastrophe. Computer security incident response has become a critical business activity today, given the growing complexity and number of cyber attacks, ransomware attacks and data breaches across the globe. Without a detailed irp, organizations risk prolonged downtime, data loss, and significant. Web incident response is the structured methodology for handling security breaches and cyber attacks, including identification, investigation, containment, eradication, and recovery activities. For that, you need an incident response plan, because. Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs. Web the concept of. This segment is sponsored by graylog. Your irp will clarify roles and responsibilities and will provide guidance on key activities. Web a cybersecurity incident response plan (csirp) is the guiding light that grounds you during the emotional hurricane that follows a cyberattack.a csirp helps security teams minimize the impact of active cyber threats and outline mitigation strategies to prevent the. Web tips on how to write a cybersecurity incident response plan. Relying on his more than 10 years of security and it expertise to understand and devise. The primary objective of an incident response plan is to manage incidents in a way that limits damage and reduces recovery time and costs. In the event of an outage, a business. The. Incident response planning often includes the following details: Testing frequency is at an organization's discretion. Web an incident response plan is a written document, formally approved by the senior leadership team, that helps your organization before, during, and after a confirmed or suspected security incident. Form a united front against an attack. Plan and coordinate a rapid response. It is now imperative to view cybersecurity from the point of view of response and recovery rather than. Web an incident response plan is your first line of defense against cyber threats. Web tips on how to write a cybersecurity incident response plan. Form a united front against an attack. The prime goal of this ir is used to allow. Web cyber security incident response plan cyber security page 4 of 12 incident response plan figure 1 incident occurrence & awareness the way an incident becomes know will have an impact on.</p> Computer security incident response has become a critical business activity today, given the growing complexity and number of cyber attacks, ransomware attacks and data breaches across the globe. Web an incident response plan is a document that outlines an organization’s procedures, steps, and responsibilities of its incident response program. Web incident response is the structured methodology for handling security breaches and cyber attacks, including identification, investigation, containment, eradication, and recovery activities. Form a united front against an attack. The templates, which can be tailored to fit the exact. An incident response plan template can help organizations outline exact instructions that detect, respond to and limit the effects of security incidents. Computer security threat response policy cyber incident response standard incident response policy planning policy protect: Web an incident response plan template is a comprehensive checklist of the roles and responsibilities of an incident response team in the event of a security incident. These processes reduce the time it takes the team to identify, research, contain, and extract a threat actor from systems, networks, and applications. Web regardless of the incident scope, your goal is to be able to perform the necessary steps and take into account any unexpected contingencies. This segment is sponsored by graylog. Web tips on how to write a cybersecurity incident response plan. It involves installing the security solution in software, hardware, and other technologies in the system. Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs. Web creating a robust cybersecurity incident response plan involves several key stages, each designed to prepare an organization for the identification, containment, eradication, and recovery from the cyber incident.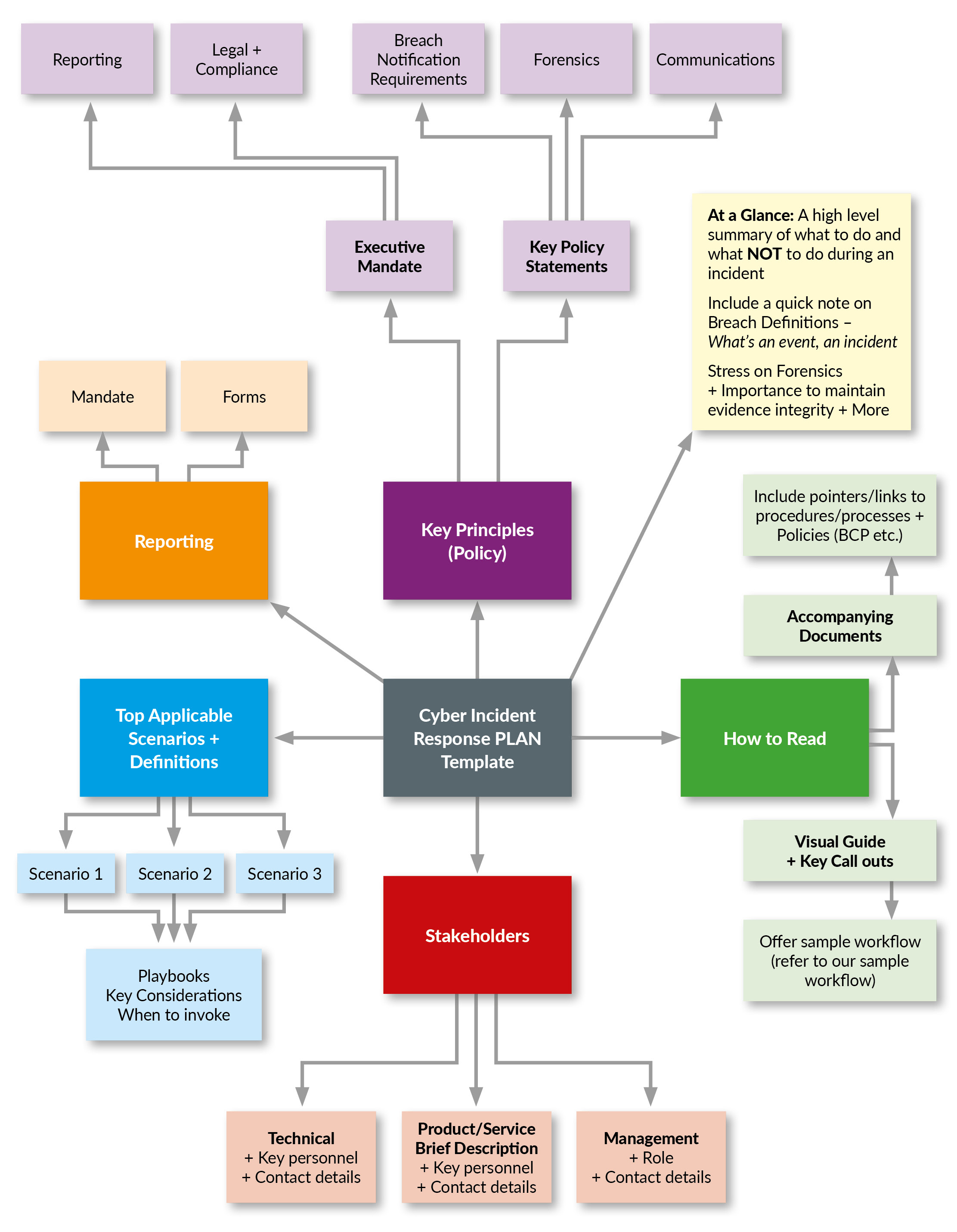
Cybersecurity Incident Response Plan Template and Example UK Cyber
Incident Response Plan Cyber Security Template
Cybersecurity Incident Response Plan {CSIRP Checklist 2023}

Vicgov Cyber Incident Response Plan Template
Cybersecurity Incident Report Template

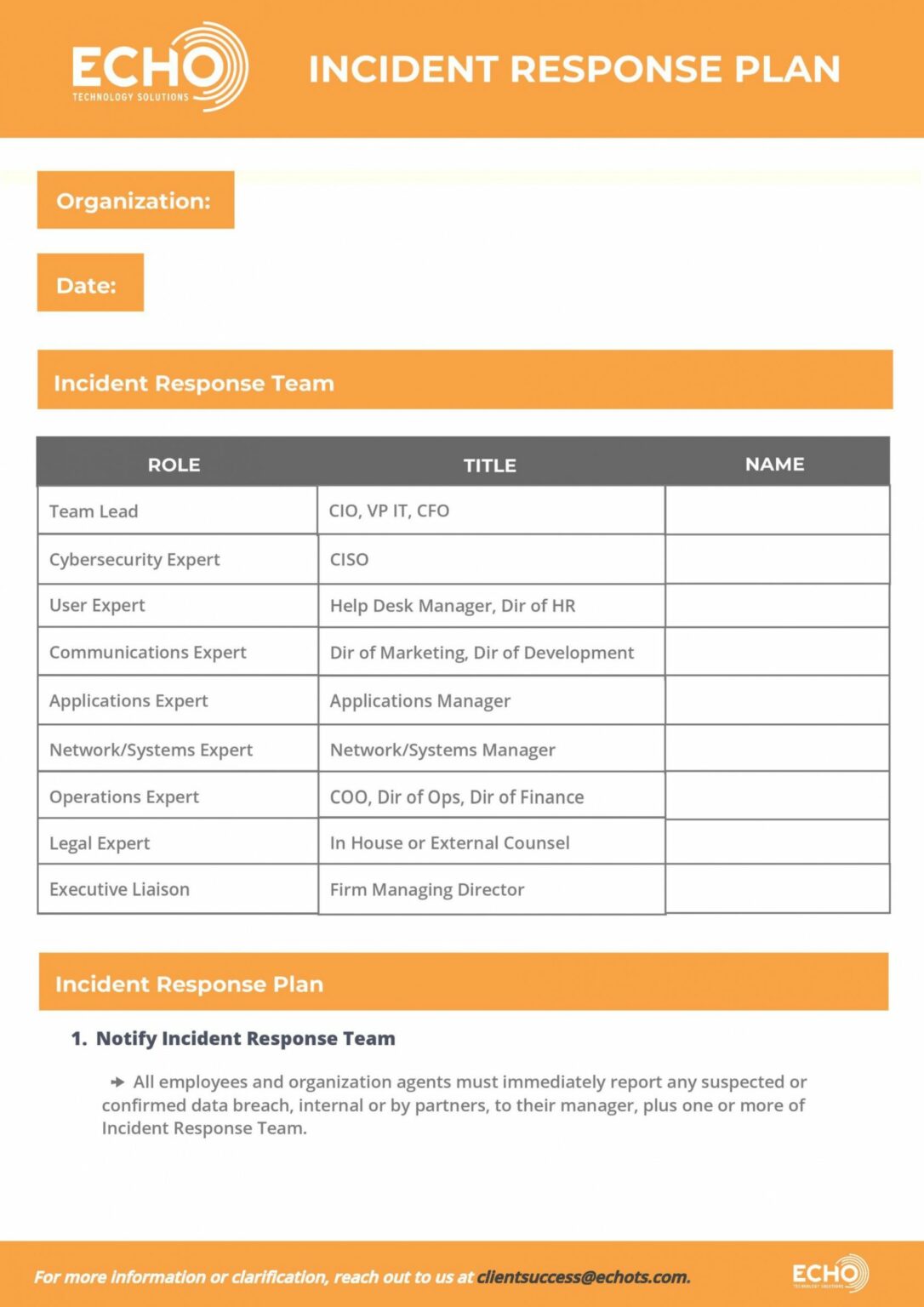
Free Cybersecurity Incident Response Plan Template Develop Your Plan

Cyber Security Incident Response Plan Template ACMP Australia and New

What is an incident response plan? Reviewing common IR templates

Nist Incident Report Template

Cyber Incident Response Checklist Business Cyber Risk
A Series Of Procedures And Different Tools Are Used And Made In Order To Identify The Root Cause Of The Problem To Eliminate Any Threats Whether Physical Or Virtual.
The Sooner A Cyber Incident Is Detected, The Better The Chances Of Minimizing Its Impact.
Web What Is A Security Incident Response Plan?
How Incident Response Supports The Organization’s Broader Mission.
Related Post: