Data Breach Incident Response Plan Template
Data Breach Incident Response Plan Template - Web sometimes called an incident management plan or emergency management plan, an incident response plan provides clear guidelines for responding to several potential scenarios, including data breaches, dos or ddos attacks, firewall breaches, malware outbreaks, insider threats, data loss and other security breaches. It should also involve communication strategies to manage the public perception of the breach and maintain transparency. A cybersecurity incident response plan (csirp) is the guiding light that grounds you during the emotional hurricane that follows a cyberattack. Web an incident response plan template is a comprehensive checklist of the roles and responsibilities of an incident response team in the event of a security incident. Upon further investigation, we discovered that a threat actor had accessed dropbox sign customer information. Web do you need a guide to develop and implement an incident response plan for your organization? This factsheet provides an overview of an incident response plan and how it should be implemented before, during, and after a cybersecurity incident. Best practices & examples (free template) 3 january 2020. Web incident response plan (irp) basics. Web a good cybersecurity incident response plan template is designed to guide an organization through the process of recovering from a cybersecurity incident, such as a data breach, ransomware attack, or system compromise. Web sometimes called an incident management plan or emergency management plan, an incident response plan provides clear guidelines for responding to several potential scenarios, including data breaches, dos or ddos attacks, firewall breaches, malware outbreaks, insider threats, data loss and other security breaches. Developing your incident response plan itsap.40.003 (pdf, 283 kb ) your incident response plan includes the processes,. Should a data breach occur, the plan will serve as a roadmap, giving your team the ability to react quickly and reduce stress. The ultimate data breach response plan. Web incident response shall follow the incident response and reporting procedures specified in the security plan. Web a response plan should include steps to detect and contain the breach, assess the. Cybersecurity best practices, election security. Web sample letter from a breaching entity to notify new yorkers of a security breach incident. (pdf, 300.84 kb ) tags. Web this publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Upon learning of an incident or a data spillage, the issm will take. Web blog, learning center march 24, 2021. Web incident response shall follow the incident response and reporting procedures specified in the security plan. Download this document from aicpa and learn the best practices and procedures for handling security breaches and minimizing the impact of cyberattacks. Alert your incident response team. A cybersecurity incident response plan (csirp) is the guiding light. Web do you need a guide to develop and implement an incident response plan for your organization? How to develop a data breach incident response plan guide. Web incident response shall follow the incident response and reporting procedures specified in the security plan. Web this publication provides practical guidelines on responding to cyber security and data breach incidents in a. The response to the threat should also be reviewed to see how effective the response was, and if there is anything that. The plan establishes a team of first responders to an incident with defined roles, responsibilities, and means of communication. After the incident, it is important to review how the breach happened and what needs to be improved on. This factsheet provides an overview of an incident response plan and how it should be implemented before, during, and after a cybersecurity incident. (pdf, 300.84 kb ) tags. It also describes the steps and actions required to detect a security incident, understand its impact, and control the damage. Web the 5 essential data breach incident response plan action items. This. Web a good cybersecurity incident response plan template is designed to guide an organization through the process of recovering from a cybersecurity incident, such as a data breach, ransomware attack, or system compromise. What actions need to take place, when and how they need to occur, and who needs to be involved. Web sample letter from a breaching entity to. If you’re ready to get started, we can help. The ultimate data breach response plan. Don’t wait until it’s too late to ramp up your defences! It should also involve communication strategies to manage the public perception of the breach and maintain transparency. After the incident, it is important to review how the breach happened and what needs to be. We believe that this incident was isolated to dropbox sign infrastructure, and did not. Web do you need a guide to develop and implement an incident response plan for your organization? Cynet incident response plan template. (pdf, 300.84 kb ) tags. Web to help you respond effectively to a data breach, and to limit the effect of its damage to. On april 24th, we became aware of unauthorized access to the dropbox sign (formerly hellosign) production environment. Web the 5 essential data breach incident response plan action items. The response to the threat should also be reviewed to see how effective the response was, and if there is anything that. Should a data breach occur, the plan will serve as a roadmap, giving your team the ability to react quickly and reduce stress. Web a cyber incident response plan template developed by efforts of the australian energy sector readiness and resilience working group in 2019, specifically with support from the australian energy market operator (aemo), tasmanian department of state growth, the victorian government Cybersecurity threats come in various forms, from social engineering to database vulnerability exploitation. Web incident response shall follow the incident response and reporting procedures specified in the security plan. We believe that this incident was isolated to dropbox sign infrastructure, and did not. Web data breach response plan template. Web what is the data breach response plan template? Web incident response plan: Web to help you respond effectively to a data breach, and to limit the effect of its damage to your business, we’ve compiled a list of advice on building a data breach incident response policy as well as this helpful template to help you get started. Incident discovery and confirmation, containment and continuity, eradication, recovery, lessons learned. Upon further investigation, we discovered that a threat actor had accessed dropbox sign customer information. A cybersecurity incident response plan (csirp) is the guiding light that grounds you during the emotional hurricane that follows a cyberattack. Download this document from aicpa and learn the best practices and procedures for handling security breaches and minimizing the impact of cyberattacks.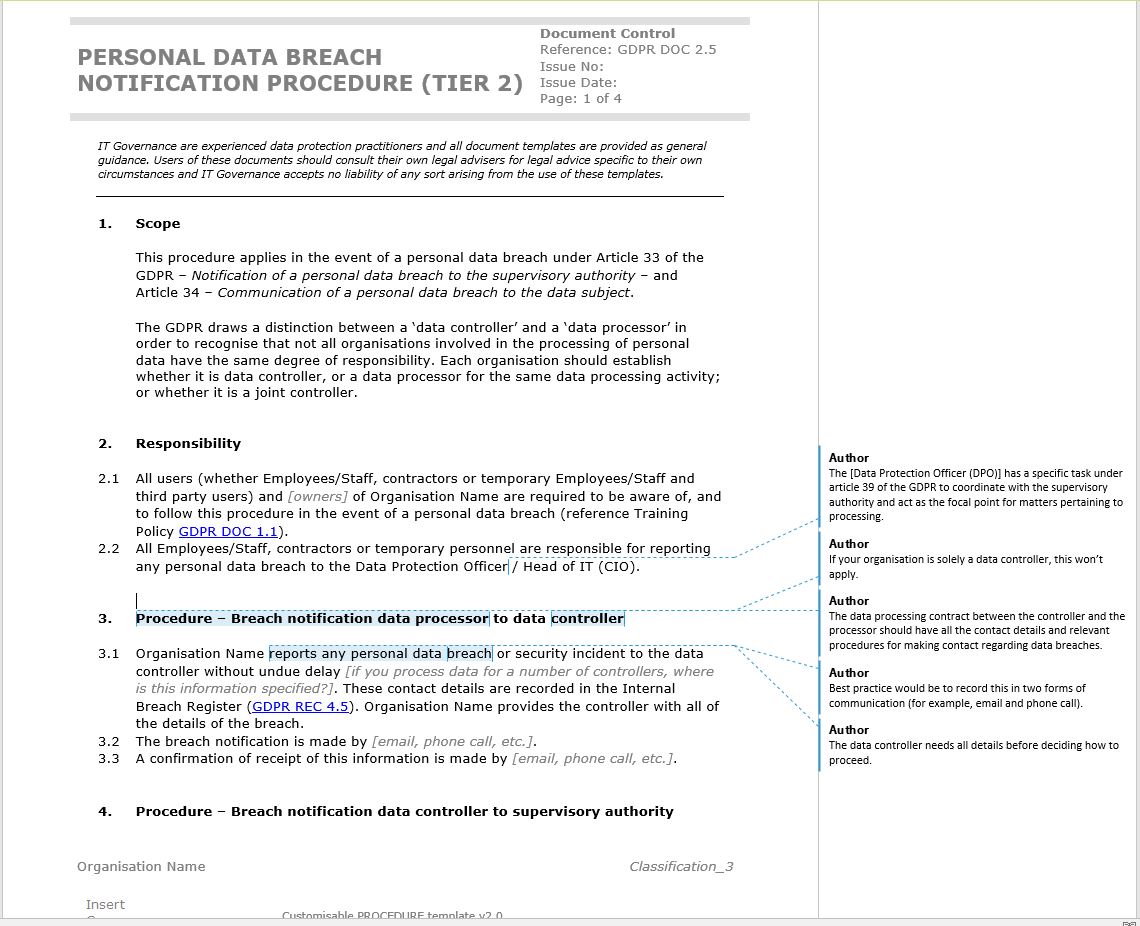
Free Template how to write a GDPR data breach notification procedure
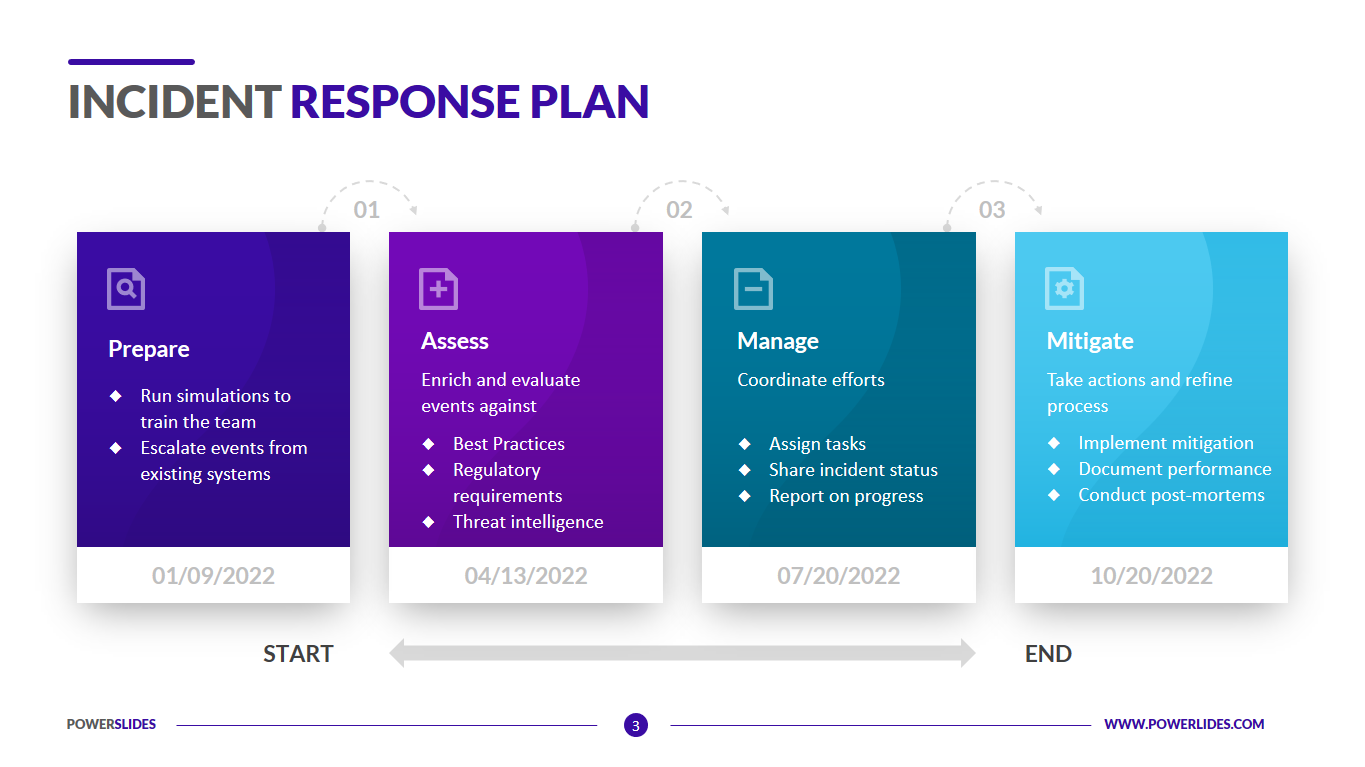
Simple Incident Response Plan Template
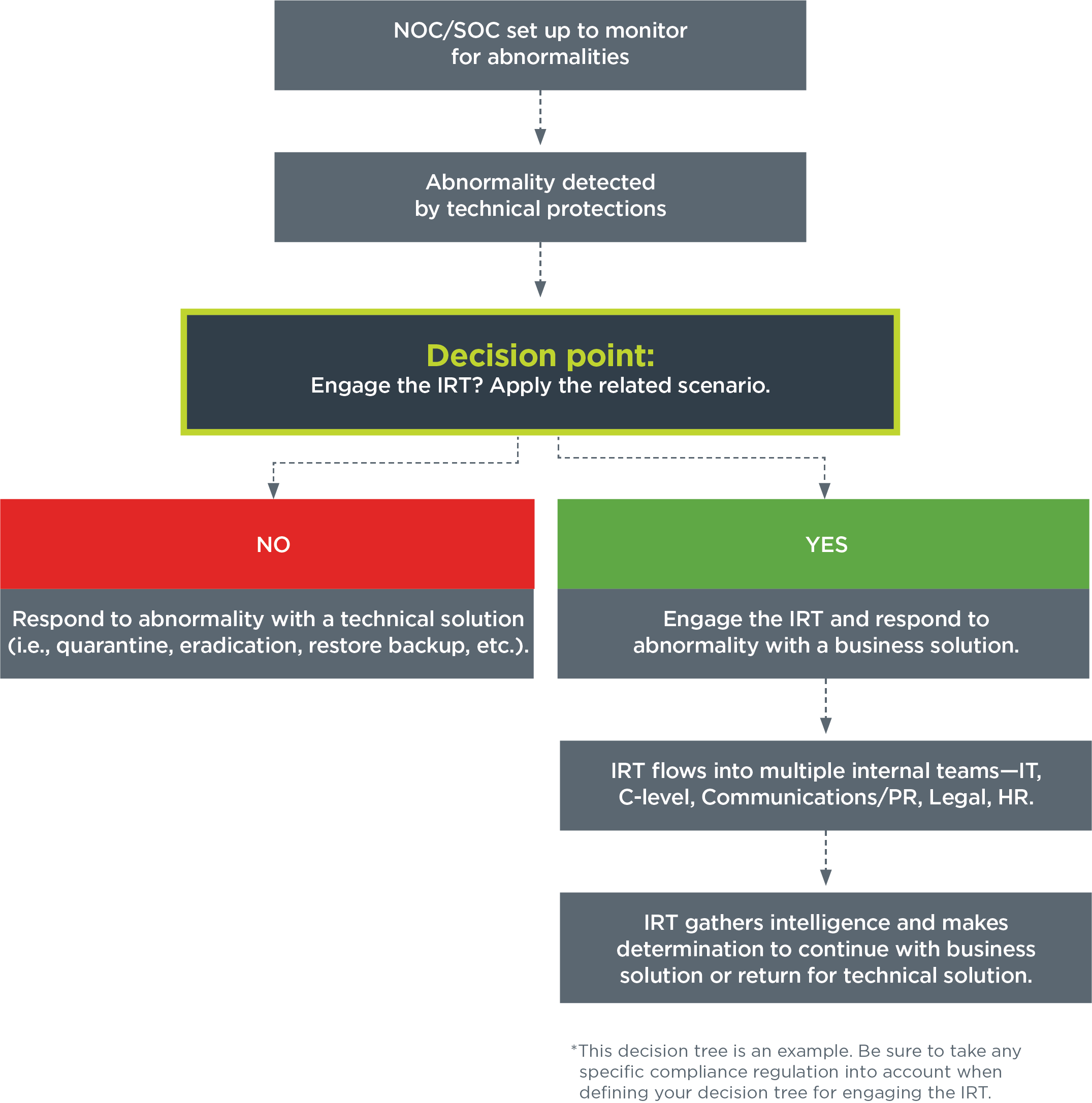
Data Breach Response Plan Template for MSPs Cybersecurity CompTIA

Data Breach Management Plan Empower IT Solutions

FREE Data Breach Response Plan Template HRLocker
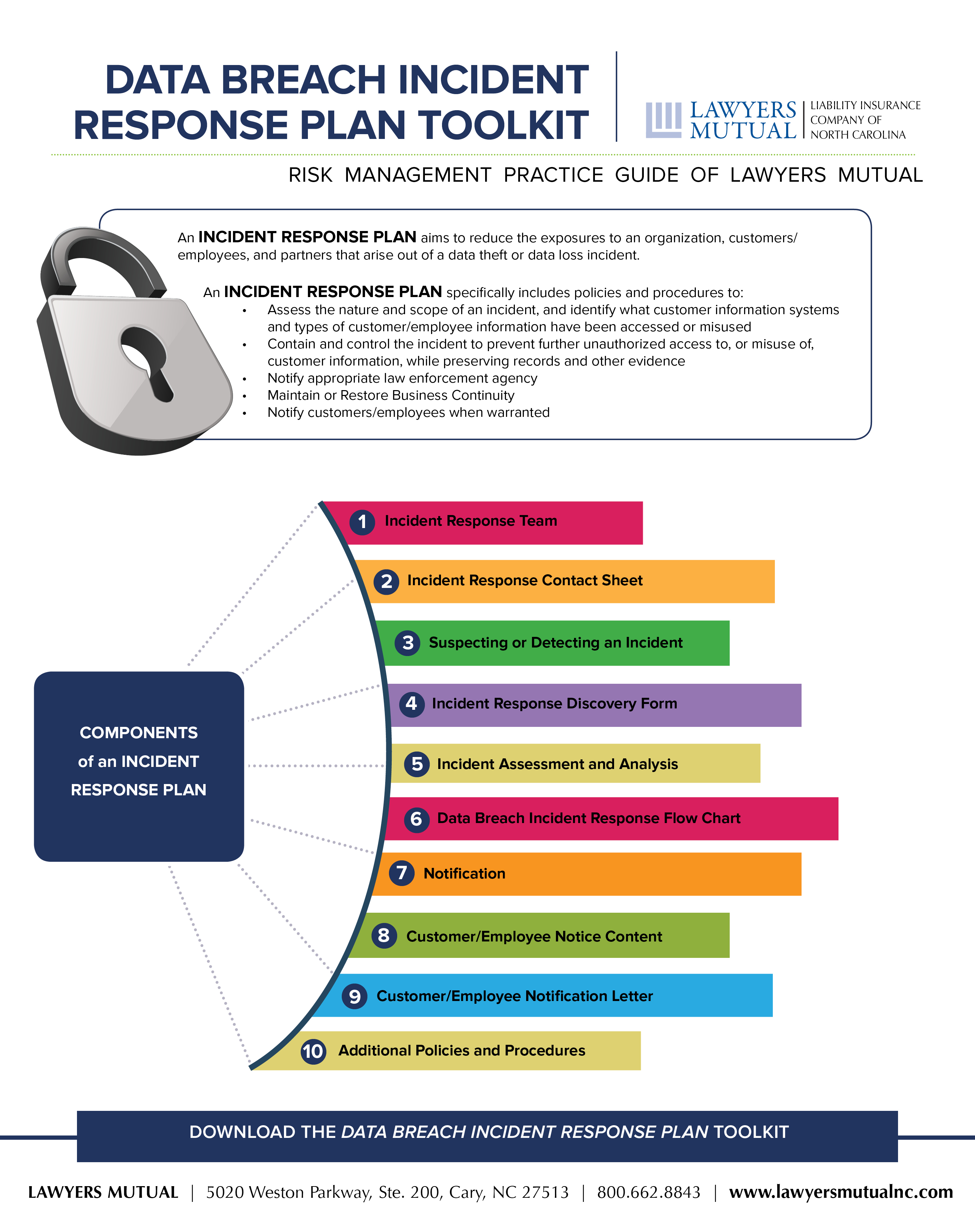
Data Breach Incident Response Plan Toolkit Infographic Lawyers

11+ Incident Response Plan Templates PDF, Word Format Download
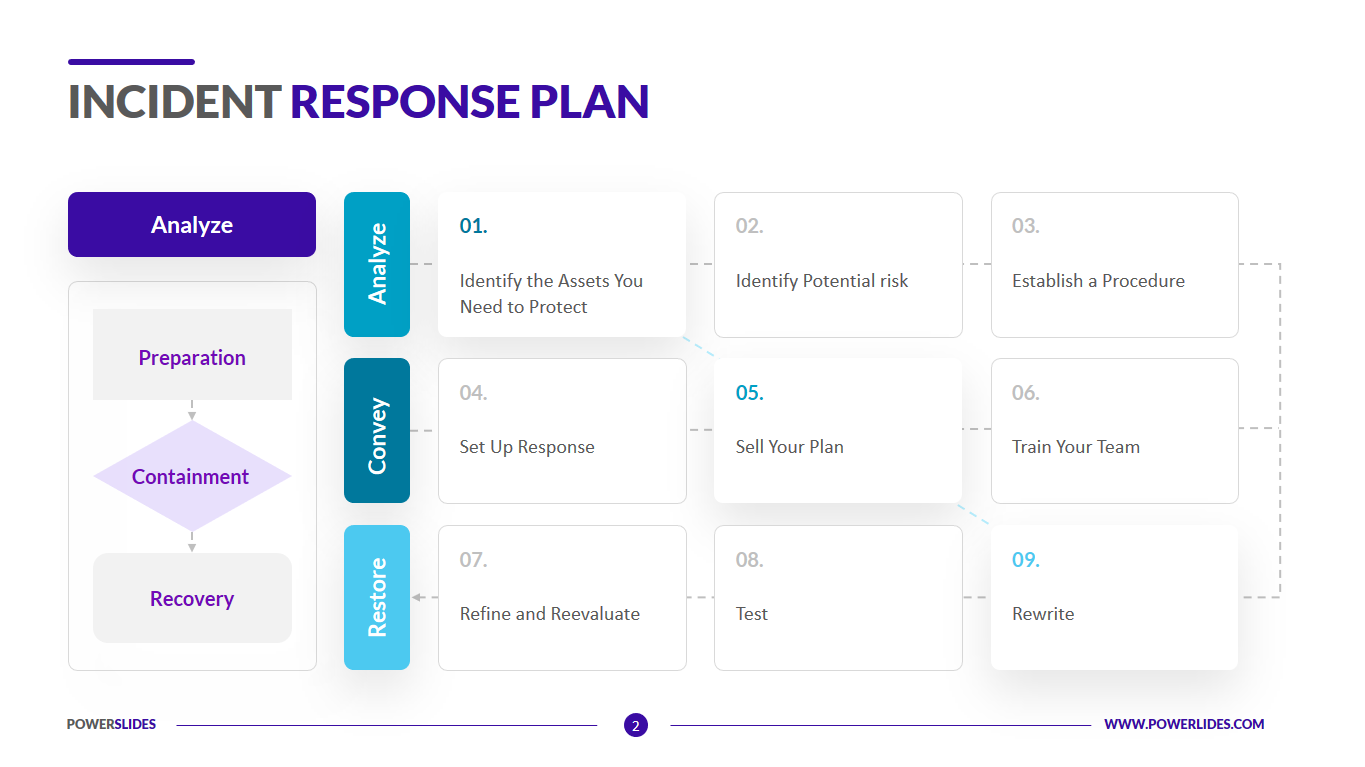
Incident Response Plan Template IT, Security and Data Professionals
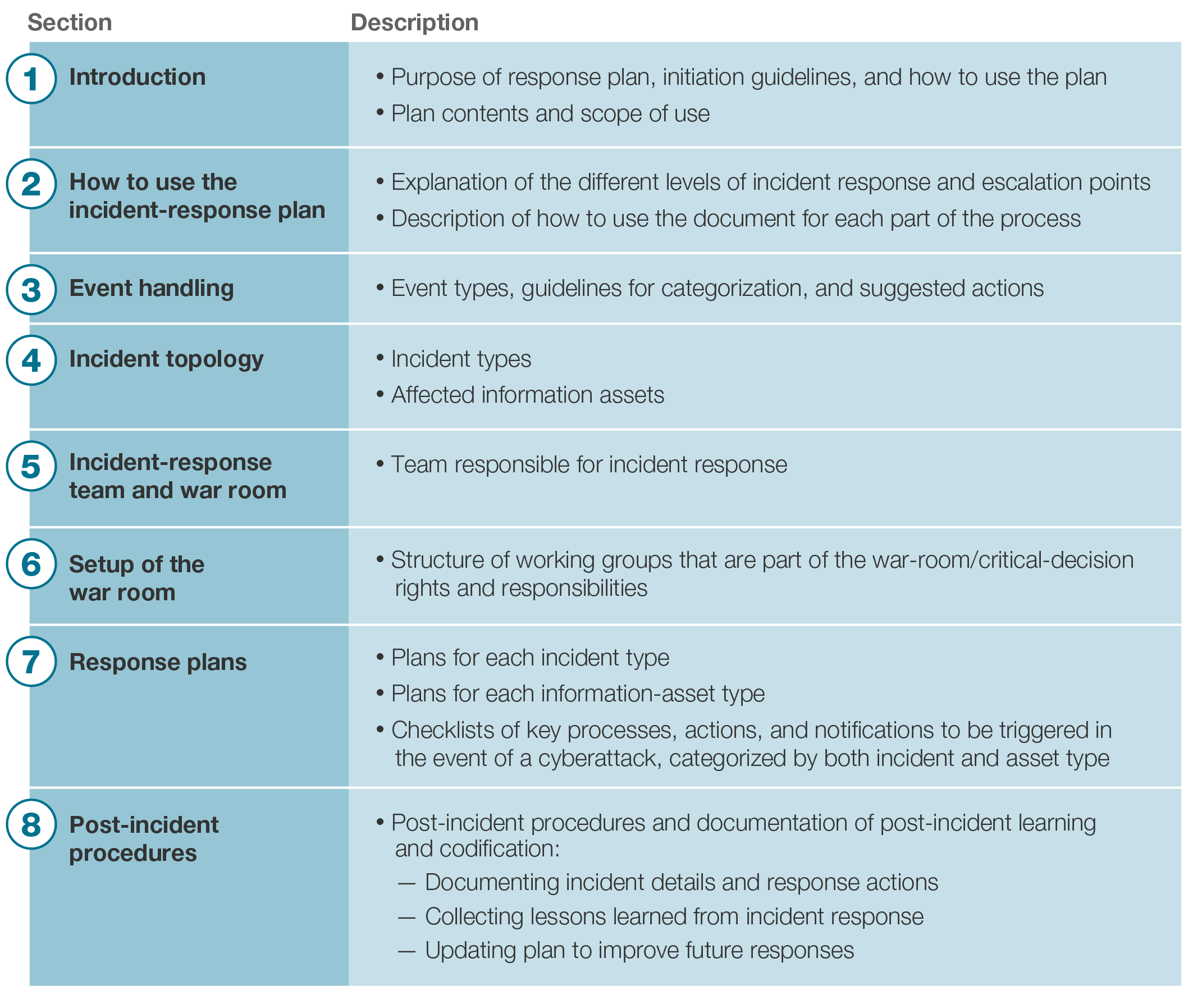
Build an Incident Response Plan Before an Incident Transpires ALIS
Data Breach Response Plan Template ER Strategies
Cynet Incident Response Plan Template.
Web Data Breach Templates & Best Practices For 2019.
What Actions Need To Take Place, When And How They Need To Occur, And Who Needs To Be Involved.
Web Learn How To Respond To A Data Breach Within Your Organization With Comptia’s Plan.
Related Post: