Information Technology Security Plan Template
Information Technology Security Plan Template - Web it 253 project two security plan template complete this template by replacing the bracketed text with the relevant information. Web • chapter 3 takes the reader through the steps of system security plan development. • appendix c includes references that support this publication. Asset management (id.am) 2 identify: Web last updated on march 15, 2024. Web the information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete. Each role plays a part in keeping a network secure from any threats. With the help of this ppt framework, you can plan and accomplish your yearly goals, and arrange your entire. Web establish a project plan to develop and approve the policy. Our list includes policy templates for acceptable use policy, data breach response policy, password protection policy and more. Web employment of information security analysts is projected to grow 32 percent from 2022 to 2032, much faster than the average for all occupations. Web leadership in cyberspace, the digital economy, and emerging digital technologies is central to advancing the u.s. This template provides the framework to create a comprehensive plan that meets the needs of the organization, while complying. The protection of a system must be documented in a system security plan. This free it strategic plan template spells out simple yet effective procedures for aligning it strategy with your company's strategic objectives and initiatives. Web • chapter 3 takes the reader through the steps of system security plan development. It also needs to be flexible and have room. Schedule management briefings during the writing cycle to ensure relevant issues are addressed. It should cover all software, hardware, physical parameters, human resources, information, and access control. It provides institutional memory that survives. One new control and three supporting control enhancements related to identity providers, authorization servers, the protection of cryptographic keys, the verification of identity assertions and access tokens,. It may be necessary to make other adjustments as necessary based on the needs of your environment as well as other. Web an information security policy can be tough to build from scratch; Each role plays a part in keeping a network secure from any threats. Acceptable use of information technology resource policy information security policy security awareness and training. It also needs to be flexible and have room for revision and updating, and, most importantly, it needs. These policies define the university’s objectives for managing operations and controlling activities. Web • chapter 3 takes the reader through the steps of system security plan development. Sans has developed a set of information security policy templates. Web 8 free it strategic. Schedule management briefings during the writing cycle to ensure relevant issues are addressed. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. Many of those openings are expected to result from the need to replace workers. Web employment of information security analysts is projected to grow. This template provides a comprehensive framework for developing an it security plan that addresses the organization’s specific needs and goals. The meeting borrowed elements from the gordon research conferences, meaning the discussions. Web this it security plan template is designed for it leaders, managers, and teams of all sizes and industries who need to create a comprehensive plan to manage. Web 8 free it strategic planning templates and examples for cios. These are free to use and fully customizable to your company's it security practices. The completion of system security plans is a Web the objective of system security planning is to improve protection of information system resources. It should cover all software, hardware, physical parameters, human resources, information, and. This free it strategic plan template spells out simple yet effective procedures for aligning it strategy with your company's strategic objectives and initiatives. The protection of a system must be documented in a system security plan. Web • chapter 3 takes the reader through the steps of system security plan development. Sans has developed a set of information security policy. About 16,800 openings for information security analysts are projected each year, on average, over the decade. Web 8 free it strategic planning templates and examples for cios. It should cover all software, hardware, physical parameters, human resources, information, and access control. This free it strategic plan template spells out simple yet effective procedures for aligning it strategy with your company's. Web receive curated news, vulnerabilities, & security awareness tips. Vision set forth in the october 2022 national security strategy (nss) of a “free, open, secure, and prosperous world.”. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. Web the objective of system security planning is to improve protection of information system resources. Many of those openings are expected to result from the need to replace workers. With the help of this ppt framework, you can plan and accomplish your yearly goals, and arrange your entire. Here is a fantastic template that represents a strategy that needs to be incorporated for information technology security growth. The completion of system security plans is a The protection of a system must be documented in a system security plan. Asset management (id.am) 2 identify: Web leadership in cyberspace, the digital economy, and emerging digital technologies is central to advancing the u.s. It should cover all software, hardware, physical parameters, human resources, information, and access control. Web the information security plan template is designed for it teams to develop a plan to protect their organization's data and systems. Once completed, it is important that it is distributed to all staff members and enforced as stated. • appendix c includes references that support this publication. Supply chain risk management (id.sc) 3
Guide to Information Security Management Smartsheet

Free Sample Security Management Plan Template Google Docs, Word

FREE 9+ Sample IT Security Policy Templates in MS Word PDF
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
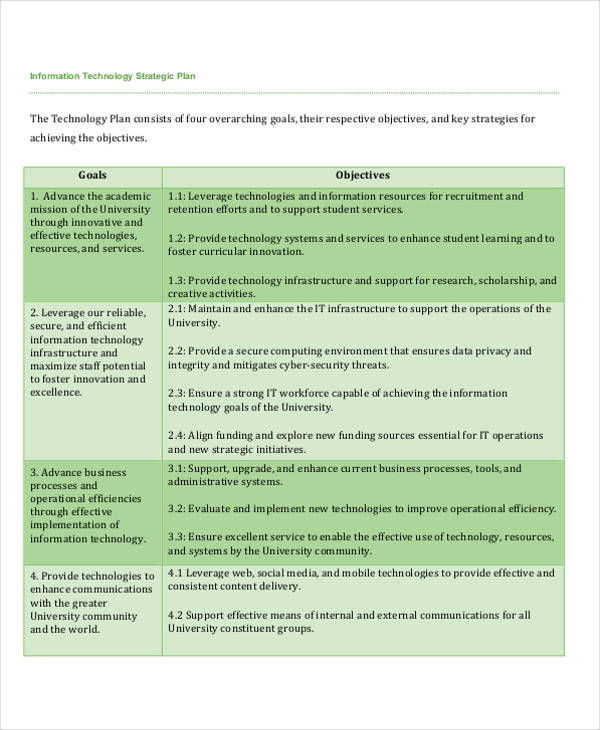
49+ Strategic Plan Templates PDF, Word
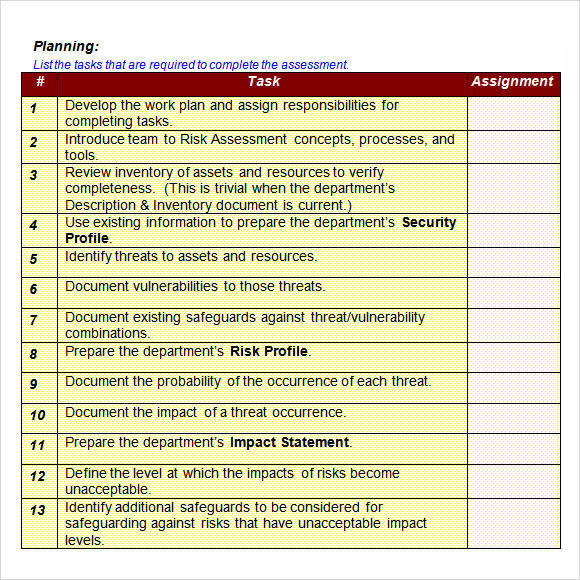
FREE 11+ Sample IT Risk Assessment Templates in PDF MS Word Excel
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-32.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
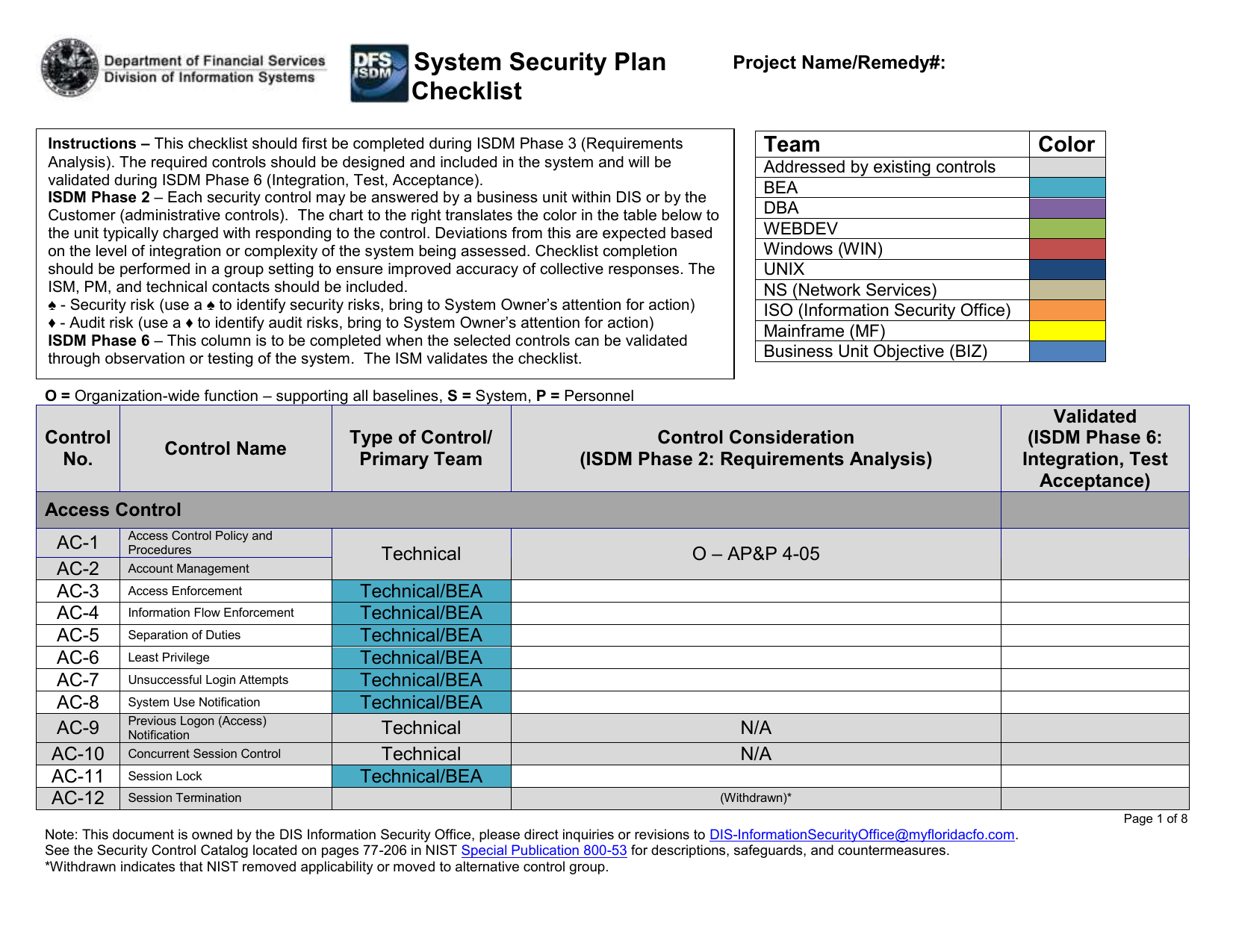
Information System Security Plan Template

FREE 15+ Sample Security Plan Templates in PDF MS Word Google Docs

Sample IT Security Policy Template 9+ Free Documents Download in Word
The Meeting Borrowed Elements From The Gordon Research Conferences, Meaning The Discussions.
• Appendix B Provides A Glossary Of Terms And Definitions.
All Federal Systems Have Some Level Of Sensitivity And Require Protection As Part Of Good Management Practice.
Schedule Management Briefings During The Writing Cycle To Ensure Relevant Issues Are Addressed.
Related Post: