Information Technology Security Policy Template
Information Technology Security Policy Template - Determine whether your grant / funding will aim to advance any sensitive technology research area. Unlike processes and procedures, policies don’t include instructions on how. Web the information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete. Use this data security policy template to start your policy and modify it to fit your business needs. A number of reputable organizations provide information security policy templates. Sans has developed a set of information security policy templates. New policy on sensitive technology research and affiliations of concern. Supply chain risk management (id.sc) 3 The purpose of this policy is to define standards and restrictions for the base configuration of internal server equipment owned and/or operated by or on the company’s internal network (s) or related technology resources via any means. Web an it security policy, also known as a cyber security policy or information security policy, sets out the rules and procedures that anyone using a company's it system must follow. An information security policy is a set of rules, guidelines, and procedures that outline how an organization should manage, protect, and distribute its information assets. Check out our library of free information technology and cyber security policy templates. An information security policy gives guidelines to employees on how to use it assets and resources within a company. Web adapt existing. Acquisition asses sment policy sans policy template: Asset management (id.am) 2 identify: Web receive curated news, vulnerabilities, & security awareness tips. Create a team to develop the policy. As the lead foreign policy agency for the united states, the department of state is advancing the. Web the cyber security policy provides guidelines to safeguard the company’s data and technology infrastructure. Web an it security policy, also known as a cyber security policy or information security policy, sets out the rules and procedures that anyone using a company's it system must follow. These guidelines apply to all users and data in an organization, preventing any security. Web a data security policy is a set of guidelines implemented by your company to protect its data against cybercrime in this age of advanced technology. Web receive curated news, vulnerabilities, & security awareness tips. Establish a project plan to develop and approve the policy. An email policy template details clear. New policy on sensitive technology research and affiliations of. Web a data security policy is a set of guidelines implemented by your company to protect its data against cybercrime in this age of advanced technology. And it defines rules and processes for protecting data confidentiality, integrity, and availability (often abbreviated as cia). Also known as information technology security refers to the practice of protecting the computer, hardware, software, servers,. In this ultimate guide i show you everything you need to know about the iso 27001 information security policy. How to comply with the new policy. For instance, the sans institute collaborated. Web the cyber security policy provides guidelines to safeguard the company’s data and technology infrastructure. Schedule management briefings during the writing cycle to ensure relevant issues are addressed. Web cisecurity.orgmsisac introduction1 nist function: Web a data security policy is a set of guidelines implemented by your company to protect its data against cybercrime in this age of advanced technology. Web information security policy templates. Web receive curated news, vulnerabilities, & security awareness tips. The policy aims to reduce the risk of data breaches, unauthorized access, and other security. Lab security policy sans policy template: As the lead foreign policy agency for the united states, the department of state is advancing the. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. The policy will usually include guidance regarding confidentiality, system vulnerabilities, security threats, security strategies. Web receive curated news, vulnerabilities, & security awareness tips. Web get ahead of your 2023 security goals. Sans has developed a set of information security policy templates. Web leadership in cyberspace, the digital economy, and emerging digital technologies is central to advancing the u.s. Supply chain risk management (id.sc) 3 Web an iso 27001 information security policy sets standards for the acceptable use of an organization’s information systems and technology, from networks and databases to software applications. Also known as information technology security refers to the practice of protecting the computer, hardware, software, servers, mobile devices, electronic systems, and data from malicious attacks that will compromise the efficiency of the. Determine whether your grant / funding will aim to advance any sensitive technology research area. Lab security policy sans policy template: Lab security policy sans policy template: How to comply with the new policy. The policy aims to reduce the risk of data breaches, unauthorized access, and other security threats by providing a structured approach to information. Web 42 information security policy templates [cyber security] a security policy can either be a single document or a set of documents related to each other. These guidelines apply to all users and data in an organization, preventing any security incidents from occurring. New policy on sensitive technology research and affiliations of concern. It addresses potential threats like human errors, hacker attacks, and system malfunctions, emphasizing proactive measures, employee responsibilities, and reporting mechanisms to maintain data integrity and security. I show you exactly what changed in. Also known as information technology security refers to the practice of protecting the computer, hardware, software, servers, mobile devices, electronic systems, and data from malicious attacks that will compromise the efficiency of the company to safeguard the confidentiality and integrity of all the access and applications. For instance, the sans institute collaborated. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. Sans has developed a set of information security policy templates. Asset management (id.am) 2 identify: Web the cyber security policy provides guidelines to safeguard the company’s data and technology infrastructure.![20+ Free Information Security Policy Templates [Word, PDF] » TemplateData](https://templatedata.net/wp-content/uploads/2021/07/intranet-and-internet-security-policy-template.jpg)
20+ Free Information Security Policy Templates [Word, PDF] » TemplateData

Free cyber security policy Docular
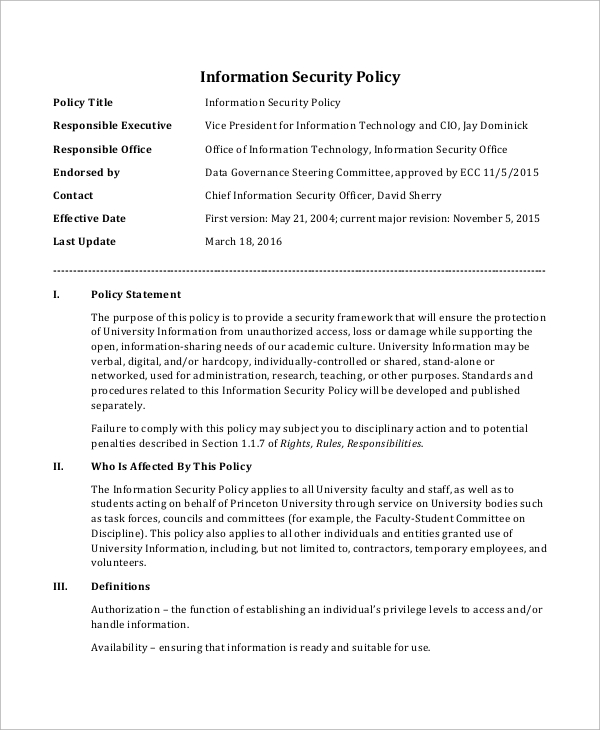
FREE 8+ Security Policy Samples in MS Word PDF

FREE 9+ Sample IT Security Policy Templates in MS Word PDF

FREE 9+ Sample IT Security Policy Templates in MS Word PDF
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](http://templatelab.com/wp-content/uploads/2018/05/Security-Policy-22.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-39.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab

Sample Information Security Policy Template locedos
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-02.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Web Receive Curated News, Vulnerabilities, & Security Awareness Tips.
For Example, A Policy Might Outline Rules For Creating Passwords Or State That Portable Devices Must Be Protected When Out Of The Premises.
An Email Policy Template Details Clear.
The Policy Will Usually Include Guidance Regarding Confidentiality, System Vulnerabilities, Security Threats, Security Strategies And Appropriate Use Of It.
Related Post: