Insider Threat Program Template
Insider Threat Program Template - Organizations of all sizes are vulnerable to an insider threat. Web this plan establishes policy and assigns responsibilities for the insider threat program (itp). Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements. Physical security, insider threat mitigation. Web before proceeding with any new process or control implementation based on the maturity analysis, insider threat, as it pertains to a particular organization, needs to. Any specific updates will most likely occur with. Malicious insider threat detection can benefit from profiling to a degree. The department of the navy (don) is working with. Prevent the unauthorized disclosure of sensitive and classified material. Web the key steps to mitigate insider threat are define, detect and identify, assess, and manage. Leverage procedures to identify and report information indicative of a potential or actual insider. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. This threat can include espionage, terrorism, sabotage, unauthorized. Web insider threat to deter employees from becoming insider threats; Threat detection and identification is the process. Web an insider threat refers to an insider who wittingly or unwittingly does harm to their organization. Physical security, insider threat mitigation. Leverage procedures to identify and report information indicative of a potential or actual insider. Web insider risk mitigation program evaluation (irmpe) related topics: Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who. Malicious insider threat detection can benefit from profiling to a degree. September kicks off national insider threat awareness month (nitam). Threat detection and identification is the process by which persons who might. Leverage procedures to identify and report information indicative of a potential or actual insider. The itp will seek to establish a secure operating environment for personnel,. Web in 2014, the national insider threat task force (nittf) published its “guide to accompany the national insider threat policy and minimum standards” to orient u.s. Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements. Web be capable of gathering relevant information across a contractor facility. This threat can include. Any specific updates will most likely occur with. Organizations of all sizes are vulnerable to an insider threat. An insider threat is the potential for an insider to use their authorized access or special. Leverage procedures to identify and report information indicative of a potential or actual insider. Web insider threat to deter employees from becoming insider threats; Cisa created the irmpe tool in collaboration with. Web insider risk mitigation program evaluation (irmpe) related topics: Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements. Web before proceeding with any new process or control implementation based on the maturity analysis, insider threat, as it pertains to a particular organization,. Malicious insider threat detection can benefit from profiling to a degree. September kicks off national insider threat awareness month (nitam). Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. Web this program will prevent espionage, violent acts against the. And mitigating the risk of an insider threat. Web find guidance developed and produced by the national insider threat task force (nittf), including a video, a guide, and a cost model template. Web be capable of gathering relevant information across a contractor facility. Web before proceeding with any new process or control implementation based on the maturity analysis, insider threat,. Web the goal of the insider threat program is to: Web be capable of gathering relevant information across a contractor facility. Leverage procedures to identify and report information indicative of a potential or actual insider. Threat detection and identification is the process by which persons who might. Malicious insider threat detection can benefit from profiling to a degree. Web the key steps to mitigate insider threat are define, detect and identify, assess, and manage. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Cisa created the irmpe tool in collaboration with. Physical security, insider threat mitigation. Web this program will prevent espionage, violent acts against the. Web be capable of gathering relevant information across a contractor facility. Organizations of all sizes are vulnerable to an insider threat. Web in 2014, the national insider threat task force (nittf) published its “guide to accompany the national insider threat policy and minimum standards” to orient u.s. Physical security, insider threat mitigation. Web before proceeding with any new process or control implementation based on the maturity analysis, insider threat, as it pertains to a particular organization, needs to. Web find guidance developed and produced by the national insider threat task force (nittf), including a video, a guide, and a cost model template. Web an insider threat refers to an insider who wittingly or unwittingly does harm to their organization. Web the goal of the insider threat program is to: Detecting insiders who pose a risk to classified information; Web this plan establishes policy and assigns responsibilities for the insider threat program (itp). The itp will seek to establish a secure operating environment for personnel,. Web insider threat to deter employees from becoming insider threats; Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. Malicious insider threat detection can benefit from profiling to a degree. Web insider risk mitigation program evaluation (irmpe) related topics: The department of the navy (don) is working with.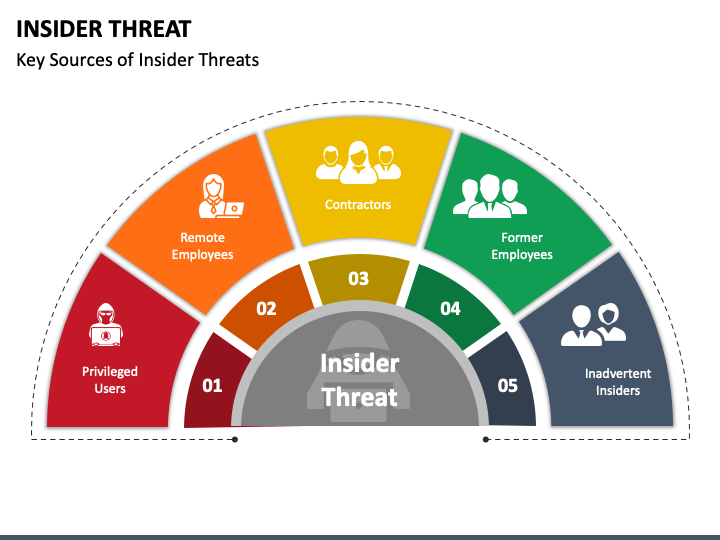
Insider Threat PowerPoint Template PPT Slides

Your Security Guide to Insider Threats Best Practices, Solutions
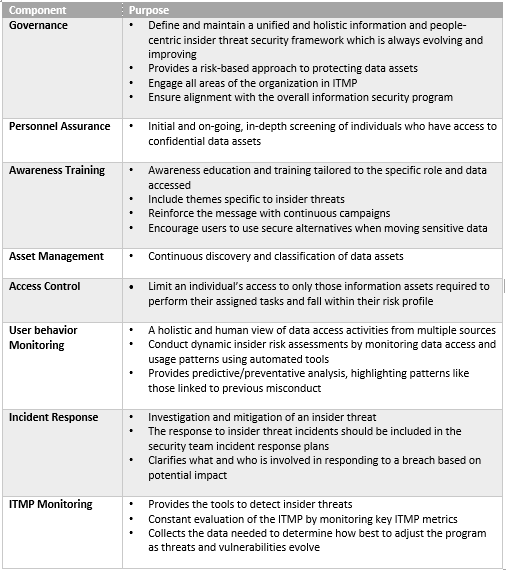
Insider Threat Plan Template
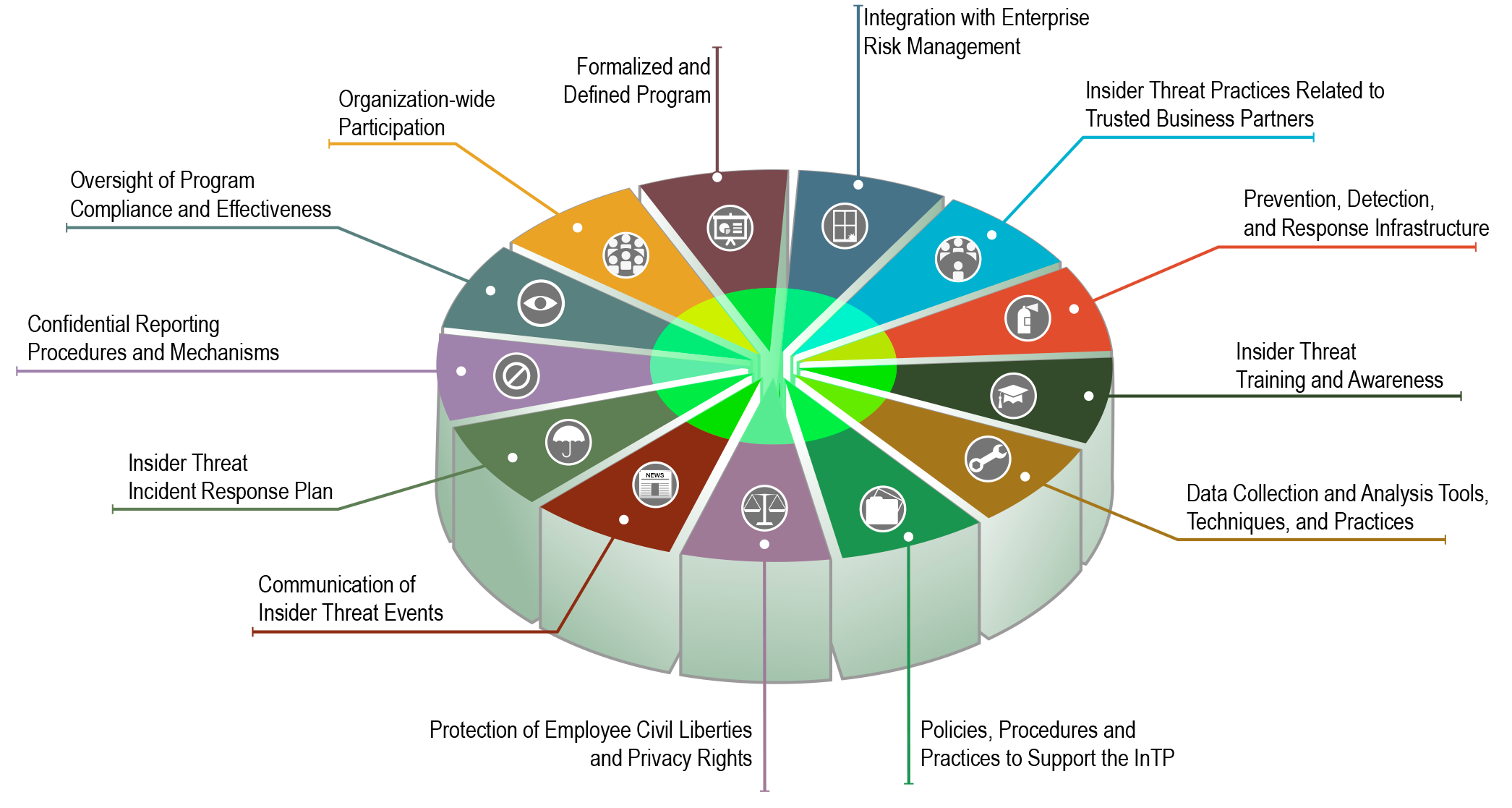
Announcing Insider Threat Program Evaluator Training from the CERT

Insider Threats and How to Detect Them IT Services CRT Utah
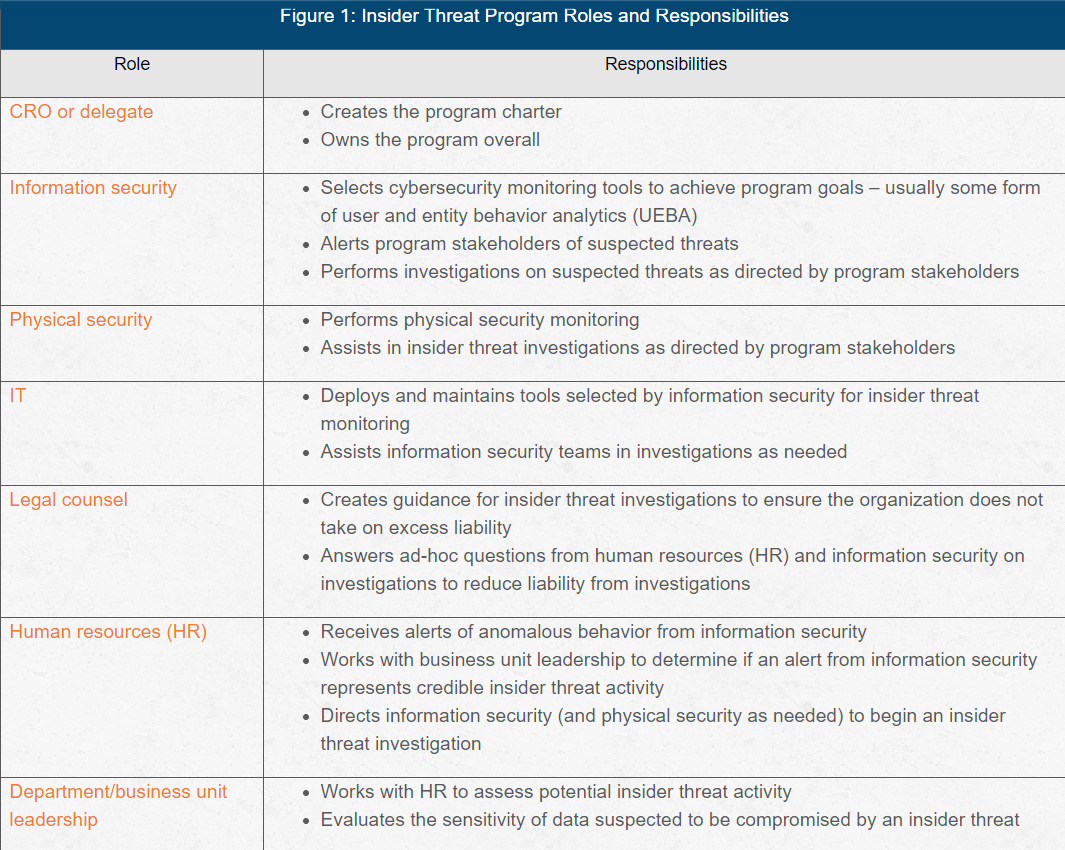
How to Establish an Effective Insider Threat Program

Insider Threat Program Template
NATIONAL INSIDER THREAT SPECIAL INTEREST GROUP INSIDER THREAT
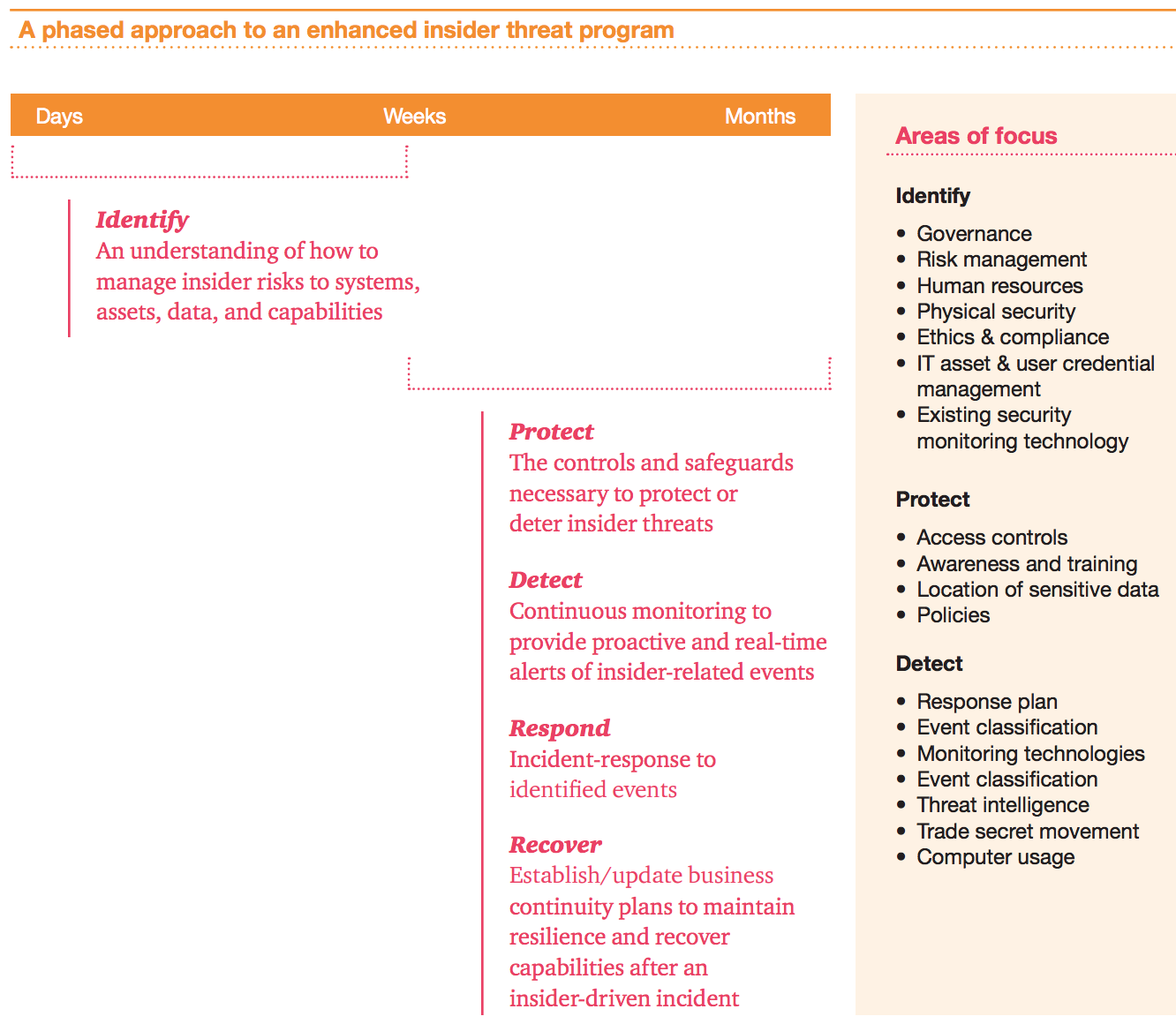
building an insider threat program Risk Management Monitor

Insider Threat Policy Template
And Mitigating The Risk Of An Insider Threat.
Malicious Insiders And Inadvertent Insiders Are Very Different.
This Threat Can Include Espionage, Terrorism, Sabotage, Unauthorized.
Web This Program Will Prevent Espionage, Violent Acts Against The Nation, Or The Unauthorized Disclosure Of Classified Information And Controlled Unclassified Information;
Related Post: