It Security Plan Template
It Security Plan Template - In addition to that, the use of a security incident response plan is to identify any threat that they come across and to help figure out a response, as well as to recover from the. It lists all the activities concerning the privacy of information, the correctness of data, and access to authorized users. Computer security incident response plan. Web the timeline to replenish social security is being extended. Establish a project plan to develop and approve the policy. This is particularly important in industries involving financial transactions, personal data, or sensitive client. Information security management (ism) sets the controls that protect confidential, sensitive, and personal information from damage, theft, or misuse. Develop an understanding of how long it would take to restore normal operations. You’ve developed, created, and implemented your security plan. 1.4 systems inventory and federal information processing standards (fips 199) Web cyber plan action items: This template provides a comprehensive framework for developing an it security plan that addresses the organization’s specific needs and goals. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. Define clear examples of your. Web security requirements spreadsheet (xlsx) security requirements. But that doesn’t mean your work is done. Web this it security plan template is designed for it leaders, managers, and teams of all sizes and industries who need to create a comprehensive plan to manage their it security. Establish security roles and responsibilities one of the most effective and least expensive means of prev enting serious cyber security incidents. Our list includes policy templates for acceptable use policy, data breach response policy, password protection policy and more. It should reflect input from various managers with responsibilities concerning the system, including information owners, the system owner, and the senior agency information. Web the objective of system security planning is to improve protection of information system resources. 1.4 systems inventory and. Sans has developed a set of information security policy templates. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. But that doesn’t mean your work is done. Web free it security policy template downloads! Our list includes policy templates for acceptable use policy, data breach response. In a perfect world, creating a plan to prevent cyber attacks, and including a network security device. Confidentiality, integrity, and availability of data, collectively. Define clear examples of your. • appendix a provides a system security plan template. Web information is an important asset and, as such, an integral resource for business continuity and growth. Define clear examples of your. Web the department of defense’s final guidance requires the review of a system security plan (ssp) in the assessment of contract solicitation during the awards process. But that doesn’t mean your work is done. • appendix a provides a system security plan template. Develop an understanding of how long it would take to restore normal. Once you know what you're up against, you need to do an honest assessment of your organization's cybersecurity maturity. The completion of system security plans is a. 1.4 systems inventory and federal information processing standards (fips 199) It provides a comprehensive structure to define objectives, set measurable targets (kpis), and implement related projects to achieve those objectives. The department of. Des moines police say they will have extra security at des moines schools on monday after a threat to a high school. Schedule management briefings during the writing cycle to ensure relevant issues are addressed. Each section includes a blue box of text like this which describes what the section is looking for and how to complete it. Web this. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. The protection of a system must be documented in a system security plan. 1.4 systems inventory and federal information processing standards (fips 199) Without an ssp, dod contractors. Sans has developed a set of information security policy. Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization’s corporate resources and proprietary information. Web security requirements spreadsheet (xlsx) security requirements csv readme for csv (txt) cui plan of action template (docx) cui ssp template **[see planning note] (docx) mapping: Web the department of defense’s final guidance requires the review of. Define clear examples of your. Acceptable use of information technology resources policy information security policy personnel security policy physical and environmental. Establish a project plan to develop and approve the policy. But that doesn’t mean your work is done. The department of homeland security homed in on resilience. • appendix c includes references that support this publication. Without an ssp, dod contractors. Web • chapter 3 takes the reader through the steps of system security plan development. Web the cyber security management plan template aims to provide quick solutions when required. These are free to use and fully customizable to your company's it security practices. The completion of system security plans is a. You’ve developed, created, and implemented your security plan. Web adapt existing security policies to maintain policy structure and format, and incorporate relevant components to address information security. Web the objective of system security planning is to improve protection of information system resources. Web implementing pindrop’s technology in a call center can significantly enhance security measures, ensuring that customer interactions are protected from fraudulent activities and that sensitive information remains confidential. Schedule management briefings during the writing cycle to ensure relevant issues are addressed.
FREE 15+ Sample Security Plan Templates in PDF MS Word Google Docs

IT Security Business Plan Template Download in Word, Google Docs

IT Security Business Plan Template Download in Word, Google Docs
![14+ FREE Security Plan Templates [Edit & Download]](https://images.template.net/45975/IT-Security-Business-Plan-Template.jpeg)
14+ FREE Security Plan Templates [Edit & Download]
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab

Guide to Information Security Management Smartsheet

10+ IT Security Policy Templates Sample Templates
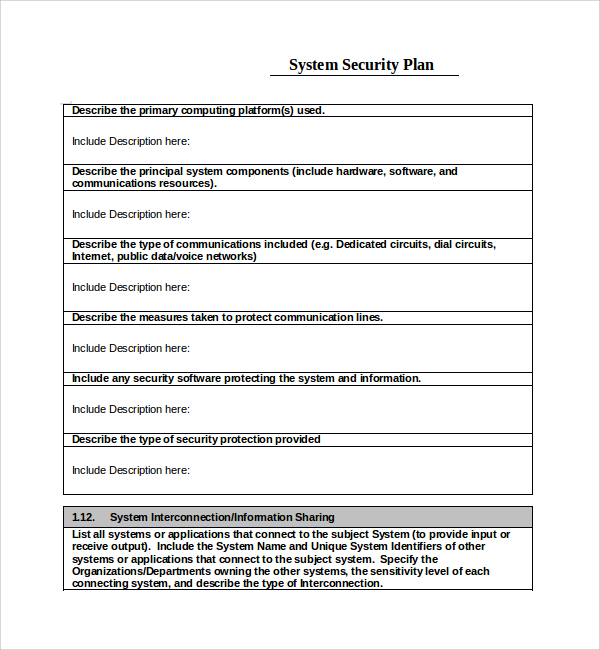
FREE 15+ Sample Security Plan Templates in PDF MS Word Google Docs
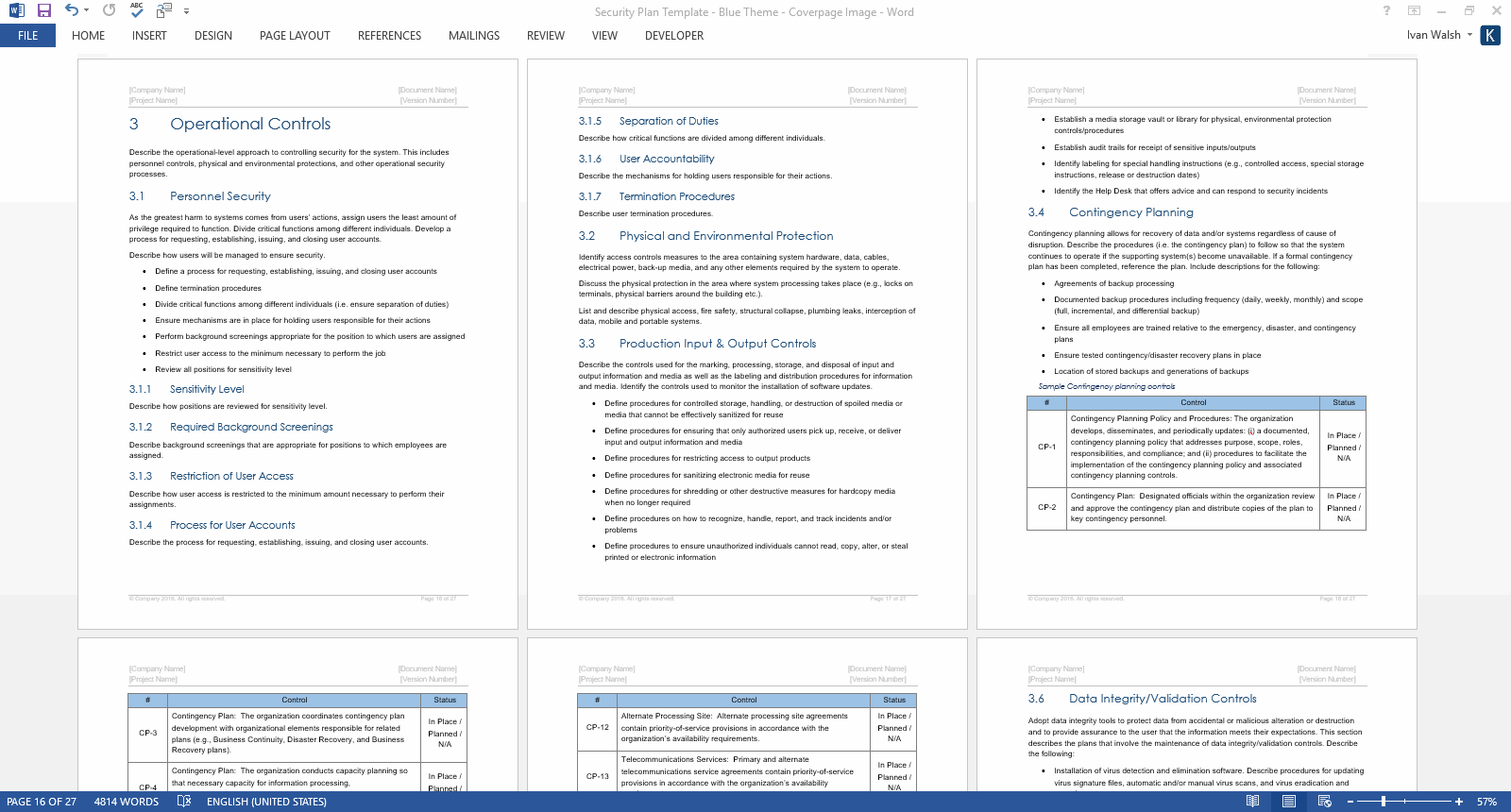
Security Plan Template (MS Word/Excel) Templates, Forms, Checklists

10+ IT Security Policy Templates Sample Templates
In A Perfect World, Creating A Plan To Prevent Cyber Attacks, And Including A Network Security Device.
Web The Biden White House Issued A National Strategy For Dealing With Cyber.
Resist The “It Can’t Happen Here” Pattern Of Thinking.
The Goal Of Your Security Plan Is To Protect Your Small Business.
Related Post: