Least Privilege Policy Template
Least Privilege Policy Template - Web there are two types of templates available in policy sentry: Web in this post, i’ve shown two different techniques that you can use to create least privilege policies for iam. Professionalanywhere, any devicepreview changes easilycreate now Least privilege must manage access from all users not just privilege accounts. One of the biggest advantages to a least privilege strategy is the ability to lower the risk of exposure to cyberattacks and minimize any potential damage an infiltration can cause. Privileged access users must have permissions set to the lowest level of access needed to accomplish their job function. You can reference these templates directly in the aws sam template for your application, providing custom parameters as required: Web given, the more restrictive least privilege environment cannot police itself to detect inappropriate use, so the need for some level of monitoring and enforcement is required. They involve violations of least privilege best practices by business users, it teams, and third parties. The principle of least privilege can and should be applied to all of those areas an expansion of the topic of 'least privilege' has some importance because, those responsible for information security, have had some past difficulty. Web iam least privilege policy generator. Web implementing least privilege at your enterprise. Enter the below command to create a template using crud type. This guide only focuses on. Web to enforce the principle of least privilege, you need to carefully assess each application's specific access needs and create a service account with the minimum necessary privileges. A powerful policy included within the: Enterprise security involves people, process and technology. List of least privilege examples. This guide only focuses on. This principle sounds very technical, but we see examples of least privileged access everywhere in our daily lives. Local initialization (optional) other usage. Web in this post, i’ve shown two different techniques that you can use to create least privilege policies for iam. Web a minimum access policy ensures that users have the lowest level of privileges to complete necessary functions. Web a permissions template that contains the cloudformation administration role, execution role, permissions policies, and the permissions. With the rampant misuse of user credentials. A powerful policy included within the: You can reference these templates directly in the aws sam template for your application, providing custom parameters as required: The principle of least privilege can and should be applied to all of those areas an expansion of the topic of 'least privilege' has some importance because, those. The user gives this template to you, the cloud administrator, to launch. Web 20 • enforcing least privilege and separation of duties policies 21 this project aims to help organizations in the financial sector design and implement a pam 22 system that controls access to and monitors privileged accounts, controls what users can do 23 using privileged account access, and. This guide only focuses on. Web least privilege is the concept and practice of restricting access rights for users, accounts, and computing processes to only those resources absolutely required to perform legitimate functions. Least privilege must manage access from all users not just privilege accounts. Privileged account management policy template. You can reference these templates directly in the aws sam. Web for windows and mac. Web this approach minimizes risks by preventing unnecessary, potentially harmful access. In this blog, we’ll review several least privilege examples commonly seen in enterprise organizations. The principle of least privilege must be followed. Increase understanding and oversight of privileged access management with a pam policy. Windows server 2022, windows server 2019, windows server 2016, windows server 2012 r2, windows. Web 20 • enforcing least privilege and separation of duties policies 21 this project aims to help organizations in the financial sector design and implement a pam 22 system that controls access to and monitors privileged accounts, controls what users can do 23 using privileged account. This principle sounds very technical, but we see examples of least privileged access everywhere in our daily lives. Privileged account management policy template. They involve violations of least privilege best practices by business users, it teams, and third parties. Web where technically feasible privileged access users must use the university approved privileged access management system. One of the biggest advantages. Web least privilege is the concept and practice of restricting access rights for users, accounts, and computing processes to only those resources absolutely required to perform legitimate functions. Increase security by removing local admin rights on windows endpoints. This guide only focuses on. Web implementing least privilege at your enterprise. Web a permissions template that contains the cloudformation administration role,. Increase security by removing local admin rights on windows endpoints. Iam database query cheat sheet. Windows server 2022, windows server 2019, windows server 2016, windows server 2012 r2, windows. Web implementing least privilege at your enterprise. Web there are two types of templates available in policy sentry: Privilege itself refers to the authorization to bypass certain security restraints. The user gives this template to you, the cloud administrator, to launch. Web this approach minimizes risks by preventing unnecessary, potentially harmful access. Web a minimum access policy ensures that users have the lowest level of privileges to complete necessary functions. With the rampant misuse of user credentials. The principle of least privilege (polp) is a computer security concept and practice that gives users limited access rights based on the tasks necessary to their job. Web in this post, i’ve shown two different techniques that you can use to create least privilege policies for iam. Web to enforce the principle of least privilege, you need to carefully assess each application's specific access needs and create a service account with the minimum necessary privileges. Web a permissions template that contains the cloudformation administration role, execution role, permissions policies, and the permissions boundary policies for any iam identities that the second template defines. In this blog, we’ll review several least privilege examples commonly seen in enterprise organizations. Web given, the more restrictive least privilege environment cannot police itself to detect inappropriate use, so the need for some level of monitoring and enforcement is required.
The Principle of Least Privilege Identity Management Institute®

Principle Of Least Privilege Examples Least Privilege Model

The Principle of Least Privilege Identity Management Institute®

Get Started With the Principle of Least Privilege Computer Networking
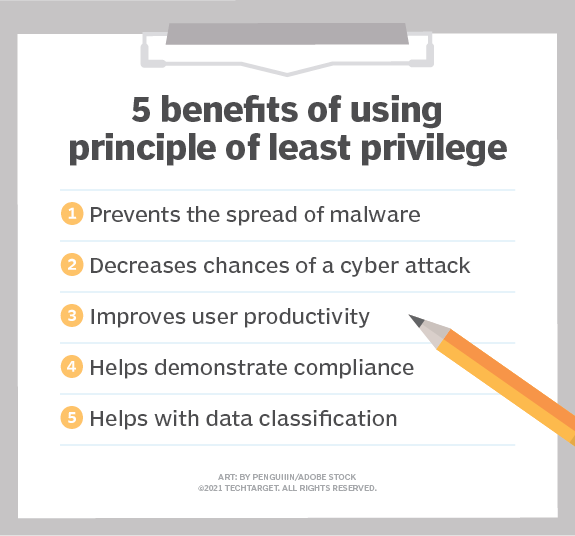
Principle of least privilege examples & best practices

What is PoLP Principle of Least Privilege? 👐

Principle of Least Privilege (PoLP) What is it & Why is it important
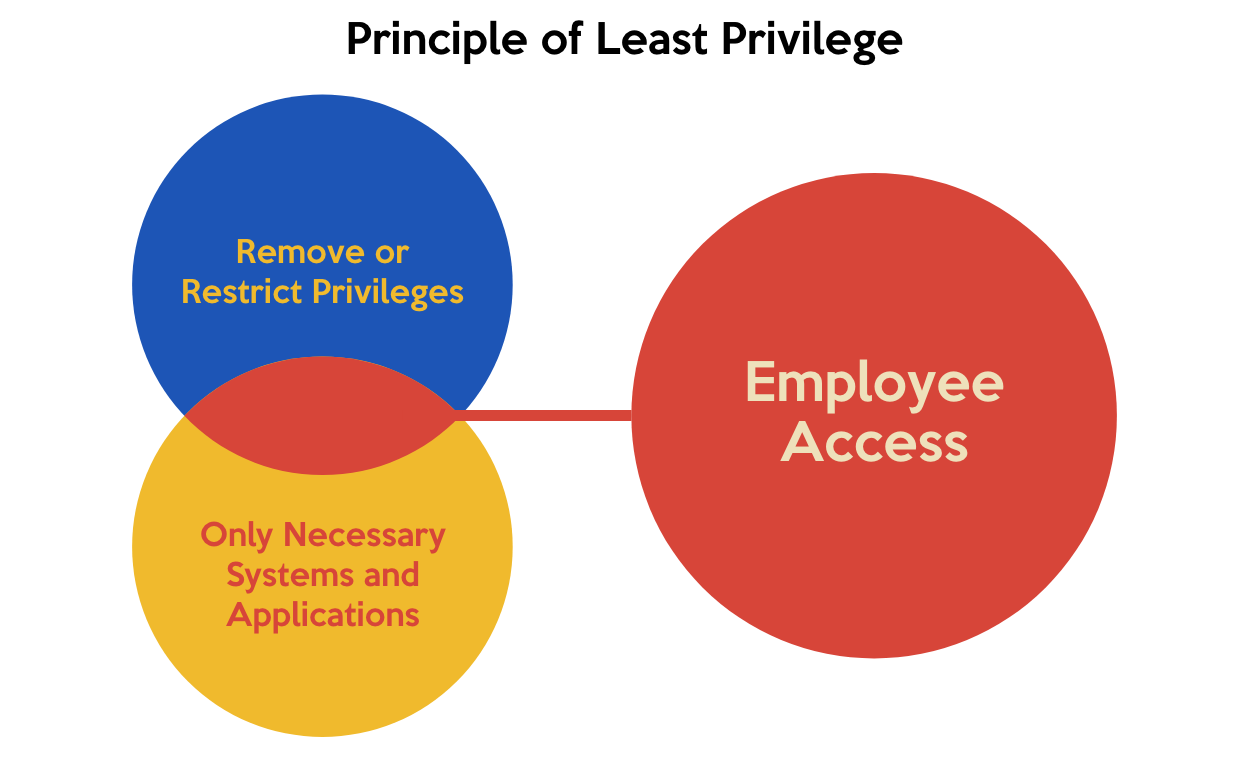
Identity & Access Management (IAM) for Dummies
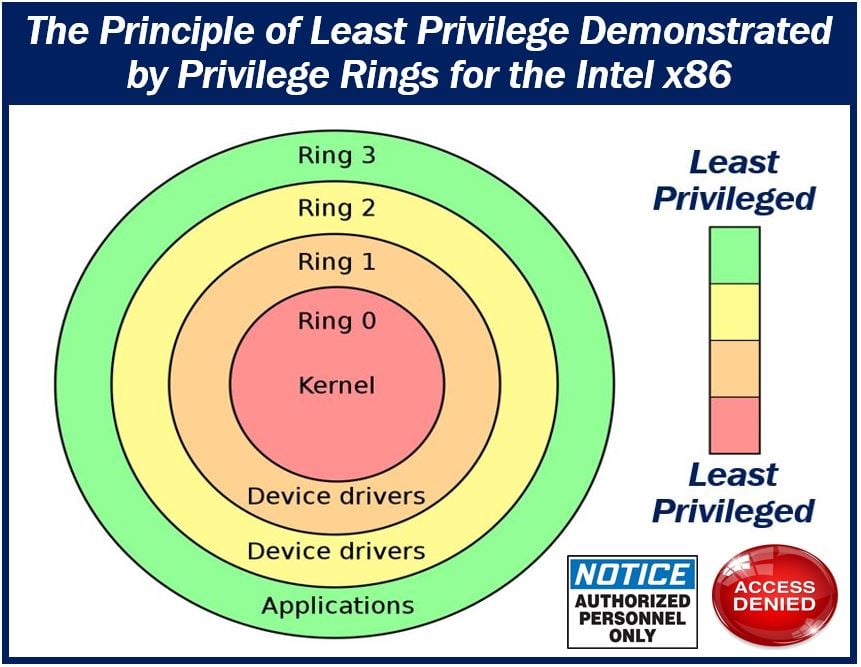
The 5 Most Important Strategies of the Security Principle of Least

How to implement the principle of least privilege with CloudFormation
Enter The Below Command To Create A Template Using Crud Type.
The Principle Of Least Privilege Access Is A Software Security Best Practice That Provides A User Only The Minimum Set Of Rights Required To Perform An Assigned Job Or Function.
With Two Versions, Complete And Standard, Kill Local Admin Rights.
Web One Of The Fastest Ways To Scope Permissions Appropriately Is To Use Aws Sam Policy Templates.
Related Post: