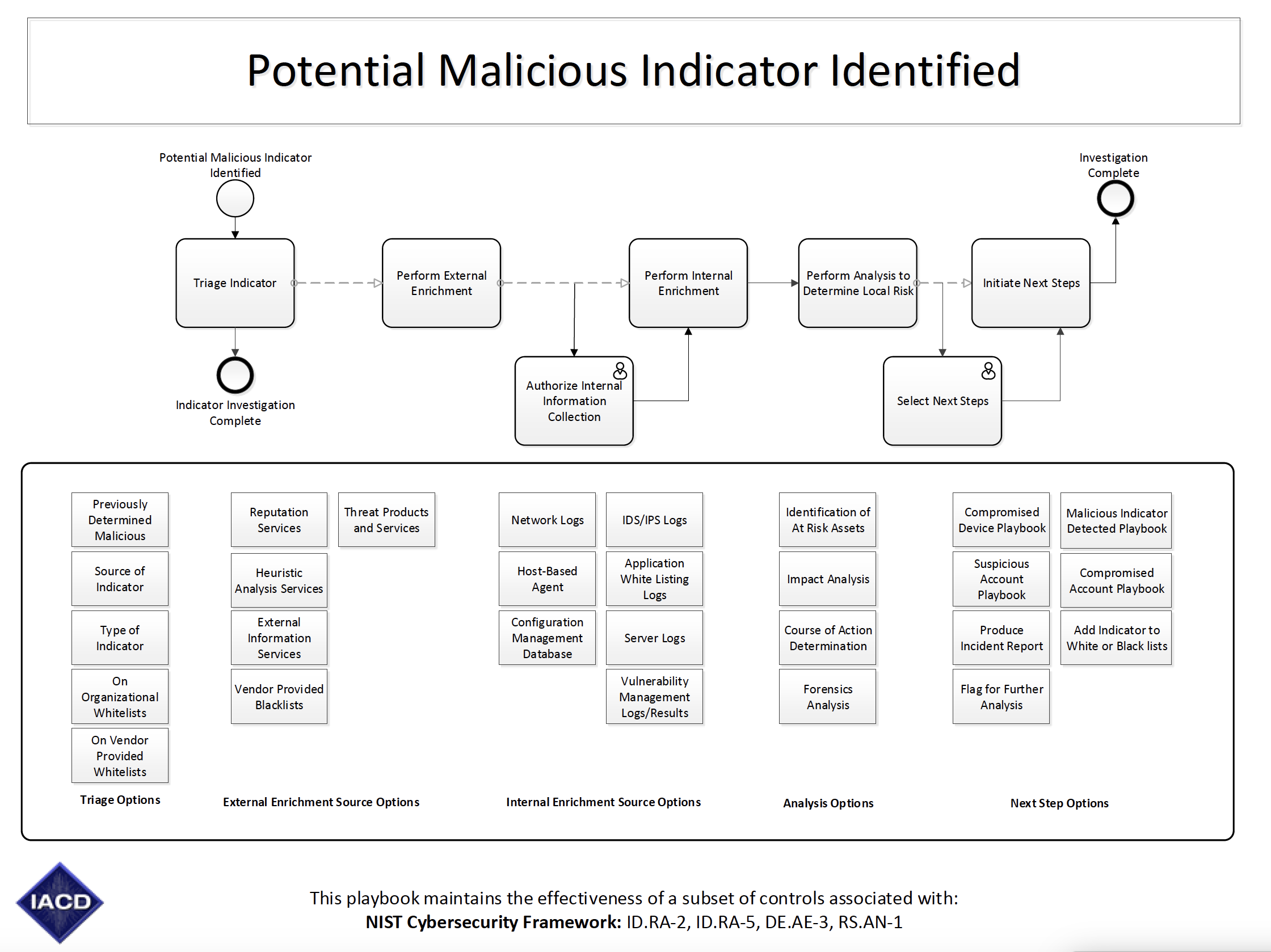
Nist Incident Response Playbook Template
Nist Incident Response Playbook Template - Web nist cybersecurity framework policy template guide. Prepare, detect, analyze, contain, eradicate,. Web the following list of templates are supporting materials to complete the steps and actions listed in the nist community resilience planning guide playbook. The immediate response, also known as triage, could. This plan refers to the scope of measures to be. Web created february 7, 2019, updated september 16, 2022. Web this article covers 5 critical steps to creating an effective incident response playbook. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. Understand the nist incident response. Web this repository contains all the incident response playbooks and workflows of company's soc. Creating and maintaining an incident response playbook can significantly improve the speed and effectiveness of your organization's incident. Web this playbook is part of the nist pack. We’ll be using our own atlassian incident management handbook as a template to. Web ransomware incident response playbook framework template. The ddos incident response playbook contains all 7 steps defined by the nist. Web here’s a look at some of the fundamental steps you can take towards building a really effective ir playbook. Prepare, detect, analyze, contain, eradicate,. Web cisa, federal government cybersecurity incident & vulnerability response playbooks; We’ll be using our own atlassian incident management handbook as a template to. Web review the following incident response playbooks to understand how to detect. Find out what you should do if you think that you have been a victim of a cyber incident. Web this repository contains all the incident response playbooks and workflows of company's soc. Here’s an example of how a. The immediate response, also known as triage, could. Web ransomware incident response playbook framework template. Web the following list of templates are supporting materials to complete the steps and actions listed in the nist community resilience planning guide playbook. Prepare, detect, analyze, contain, eradicate,. Web cyber incident management is directly proportional to your data, public trust, reputation, and a potential business loss. No integration headachesfree online demotrusted by thousands The ddos incident response playbook contains. Web here’s a look at some of the fundamental steps you can take towards building a really effective ir playbook. This plan refers to the scope of measures to be. Web this playbook is part of the nist pack. Here’s an example of how a. Web this repository contains all the incident response playbooks and workflows of company's soc. Learn how to build a ransomware ir playbook to prepare and protect your organization. The ddos incident response playbook contains all 7 steps defined by the nist incident response process: Creating and maintaining an incident response playbook can significantly improve the speed and effectiveness of your organization's incident. Web ransomware is a type of malicious attack where attackers encrypt an. Web here’s a look at some of the fundamental steps you can take towards building a really effective ir playbook. No integration headachesfree online demotrusted by thousands No integration headachesfree online demotrusted by thousands Web cyber incident management is directly proportional to your data, public trust, reputation, and a potential business loss. Web we’ll describe the national institute of standards. Web cyber incident management is directly proportional to your data, public trust, reputation, and a potential business loss. Chat support availableeasy to usebook a demo Web the unauthorized access incident response playbook contains all 7 steps defined by the nist incident response process: No integration headachesfree online demotrusted by thousands Web ransomware incident response playbook framework template. The immediate response, also known as triage, could. Find out what you should do if you think that you have been a victim of a cyber incident. We’ll be using our own atlassian incident management handbook as a template to. Learn how to build a ransomware ir playbook to prepare and protect your organization. This plan refers to the scope. Web this article covers 5 critical steps to creating an effective incident response playbook. Web cisa, federal government cybersecurity incident & vulnerability response playbooks; Web the unauthorized access incident response playbook contains all 7 steps defined by the nist incident response process: Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to. We’ll be using our own atlassian incident management handbook as a template to. Web the unauthorized access incident response playbook contains all 7 steps defined by the nist incident response process: Web ransomware incident response playbook framework template. No integration headachesfree online demotrusted by thousands Prepare, detect, analyze, contain, eradicate,. Web the following list of templates are supporting materials to complete the steps and actions listed in the nist community resilience planning guide playbook. No integration headachesfree online demotrusted by thousands Web here’s a look at some of the fundamental steps you can take towards building a really effective ir playbook. Web this playbook is part of the nist pack. Understand the nist incident response. Web the incident response playbook applies to incidents that involve confirmed malicious cyber activity and for which a major incident (as defined by the office of management. Web this article covers 5 critical steps to creating an effective incident response playbook. Web review the following incident response playbooks to understand how to detect and contain these different types of attacks: Web cyber incident management is directly proportional to your data, public trust, reputation, and a potential business loss. Prepare, detect, analyze, contain, eradicate,. The ddos incident response playbook contains all 7 steps defined by the nist incident response process: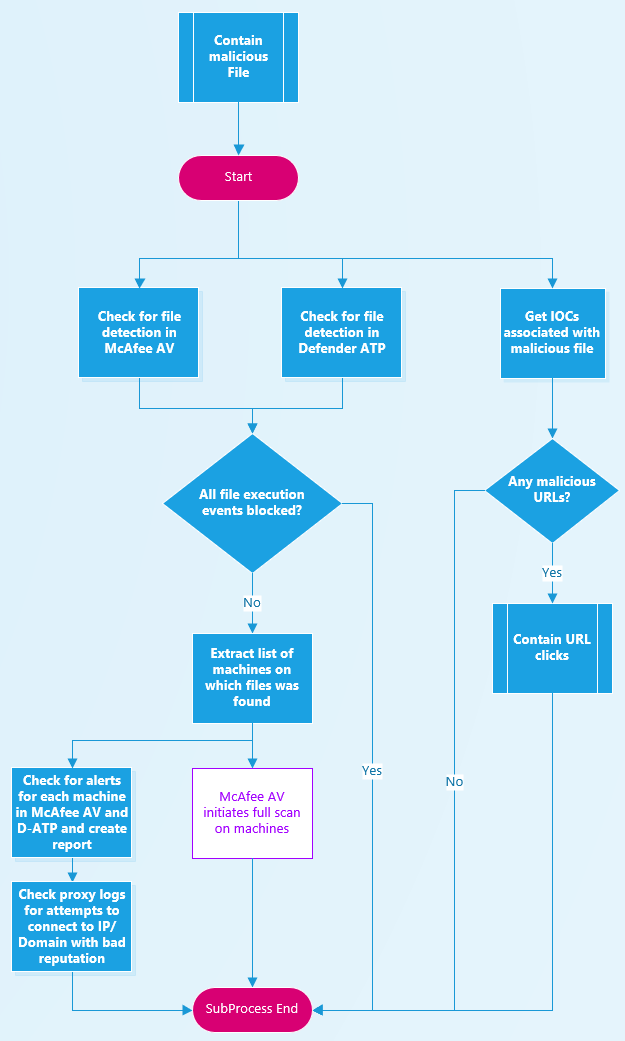
Nist Incident Response Playbook Template Portal Tutorials
Incident Response Runbook Template
NIST for Computer Security Incident Handling Clear

Incident Response Playbook Template

Developing an incident response playbook Malware News Malware
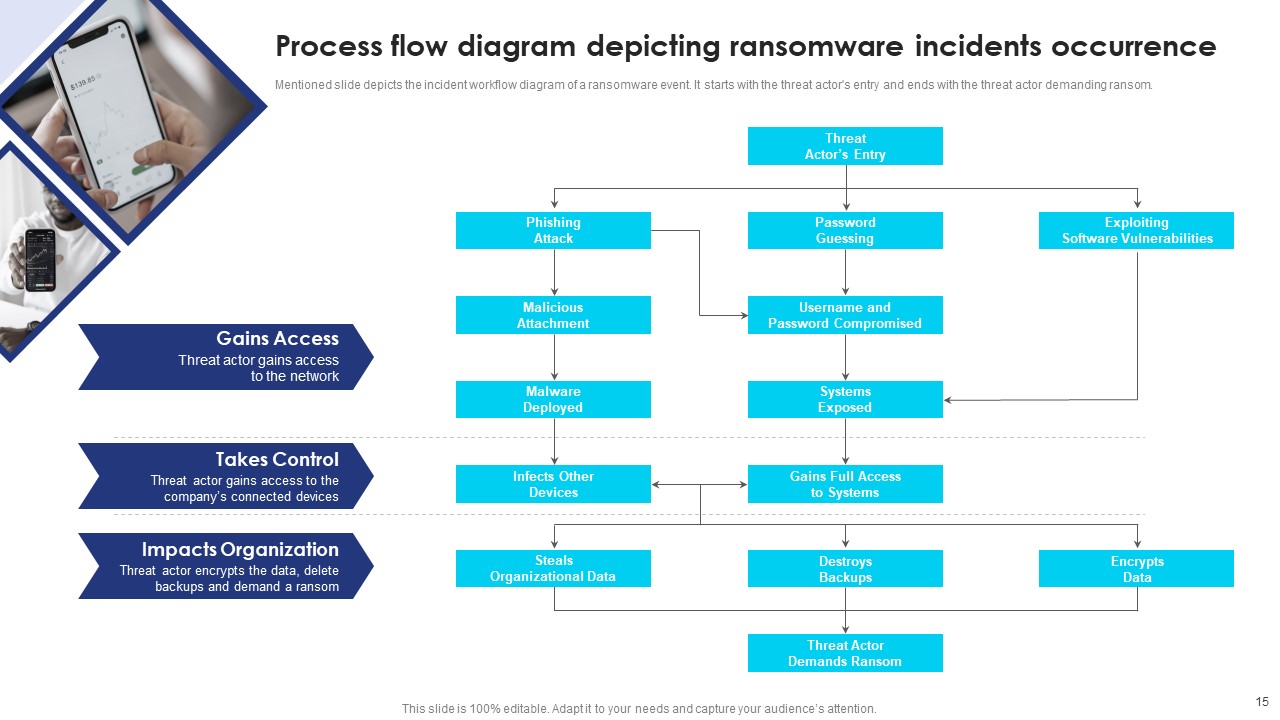
Incident Response Playbook Template
Incident Response Playbook Template Master of Documents
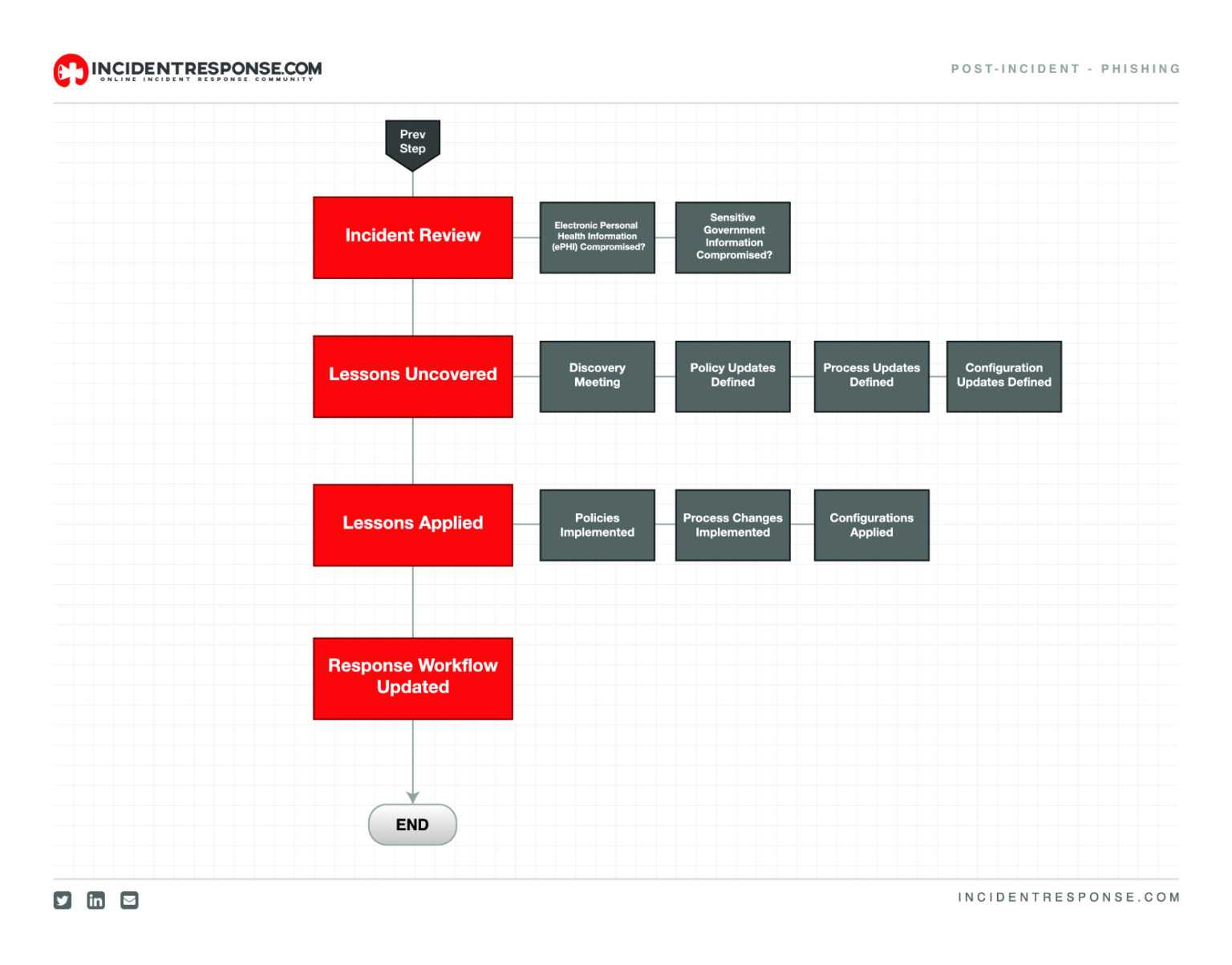
Phishing Incident Response Playbooks Gallery Throughout Incident

NIST Incident Response Playbook Template
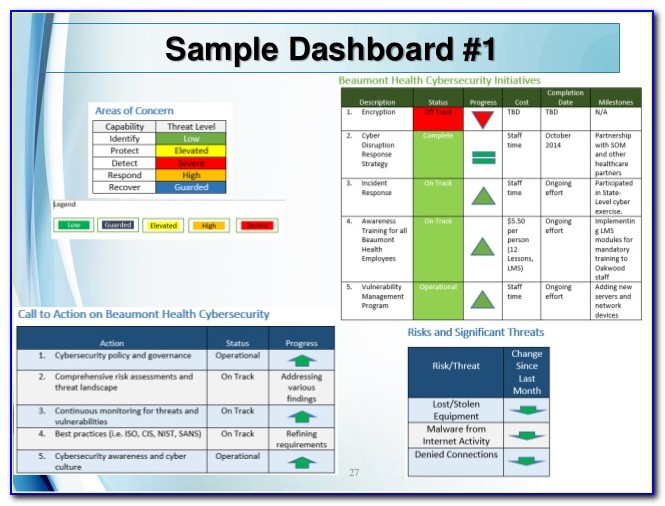
Nist Incident Response Playbook Template Portal Tutorials
Here’s An Example Of How A.
Find Out What You Should Do If You Think That You Have Been A Victim Of A Cyber Incident.
Web Ransomware Is A Type Of Malicious Attack Where Attackers Encrypt An Organization’s Data And Demand Payment To Restore Access.
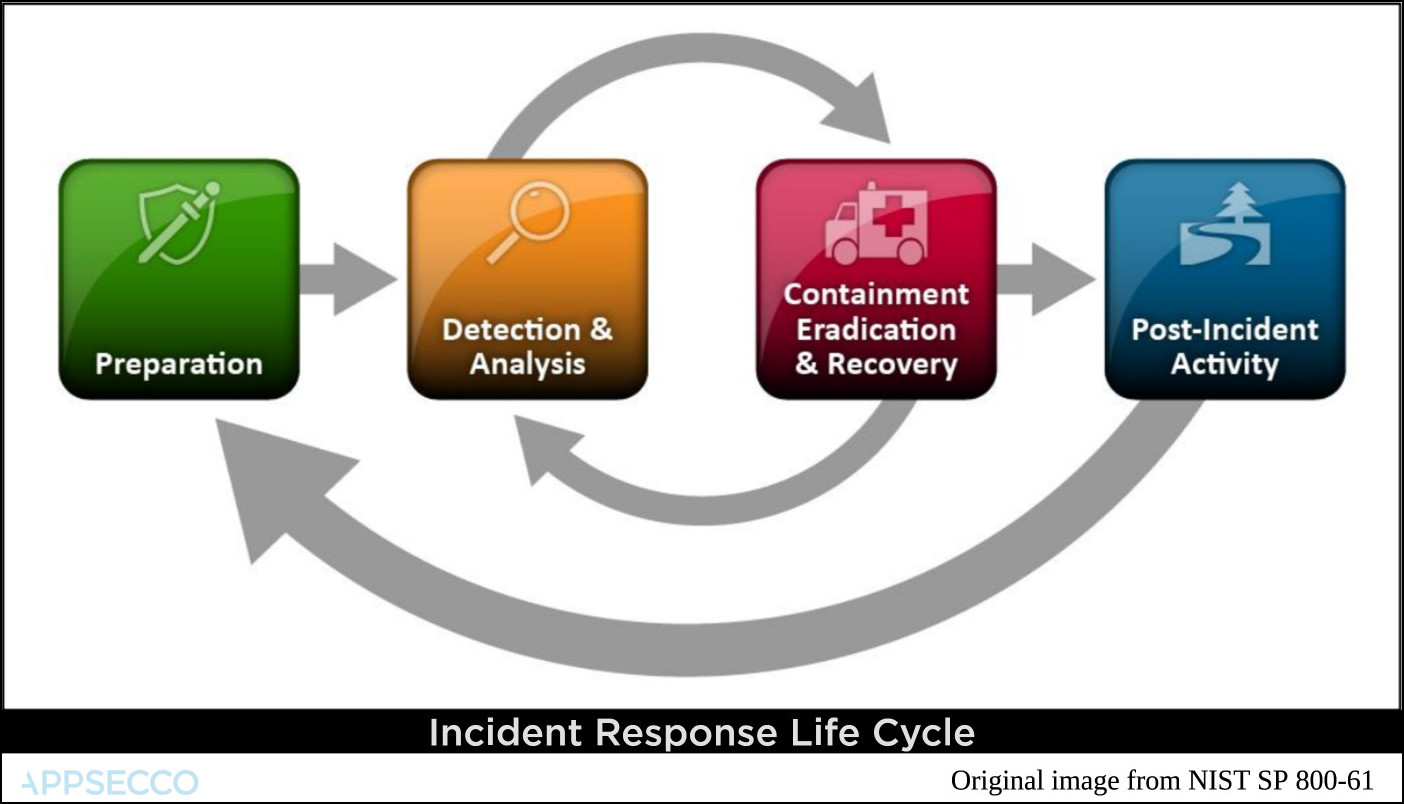
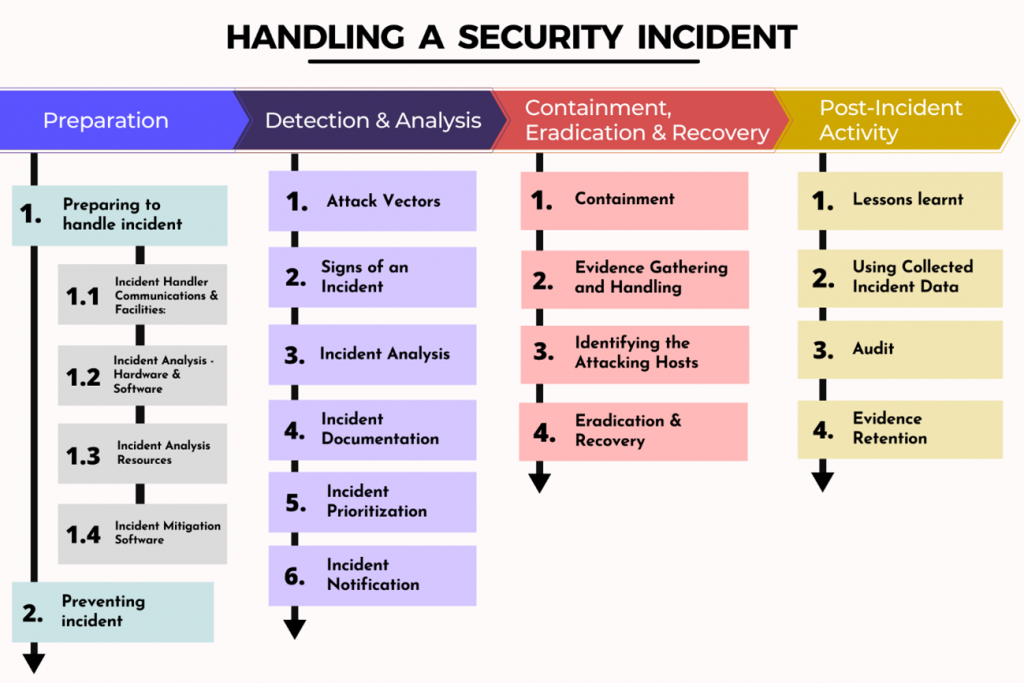
Web An Incident Response Plan Is A Set Of Instructions Designed To Help It Staff Identify, Respond To, And Recover From A Security Incident.
Related Post: