Security Log Template
Security Log Template - This easy to use template will help you figure out what initial steps you need to take to properly start. What is a daily patrol log. Web our security incident report template is provided in multiple file formats, including microsoft word, excel, and pdf. They play an important role. Date seal applied seal location name/signature. Log collection and analysis is critical for an enterprise’s ability to detect malicious activity quickly. Web created april 28, 2021, updated october 19, 2023. Whether you’re a security guard, building manager, or security firm owner, use. Web security seal log note: Included in the security shift report template. Web execute and sign your security log template with complete confidence that your document will be safeguarded and that your esignature will be legally binding and admissible in. Get your free copy now! Web download this template! What is a daily patrol log. Enter your name, date, shift start. This easy to use template will help you figure out what initial steps you need to take to properly start. Web a security log form is used by security professionals to record and document security events. Web 5.1 network access control. Web audit log management policy template for cis control 8. Use the security equipment log to track and maintain. What is the general security log. Web created april 28, 2021, updated october 19, 2023. Included in the security shift report template. They play an important role. This allows you to choose the format that best suits. Included in the security shift report template. Web download this template! Web security seal log note: They play an important role. Web need for computer security log management—the process for generating, transmitting, storing, analyzing, and disposing of computer security log data. Log files are a key part of any iso 27001 compliant information security management system (isms). Web created april 28, 2021, updated october 19, 2023. Web download this template! What is a daily patrol log. This allows you to choose the format that best suits. Web need for computer security log management—the process for generating, transmitting, storing, analyzing, and disposing of computer security log data. Whether you’re a security guard, building manager, or security firm owner, use. They play an important role. Use the security equipment log to track and maintain records of security equipment within a facility or organization, including. What is a daily. Web 5.1 network access control. This easy to use template will help you figure out what initial steps you need to take to properly start. Web need for computer security log management—the process for generating, transmitting, storing, analyzing, and disposing of computer security log data. Get your free copy now! Web use the security shift report template or go digital? 50 printable log sheet templates [direct download] most businesses use a log sheet to keep track of chronological notes or incidents that happen in the place of. This free and downloadable incident management policy template is vital for organizations seeking to protect against data breaches, ensure. The security guard daily report sample is a great way to demonstrate. Web use. Security shift report (watermarked) by 1st reporting. Log collection and analysis is critical for an enterprise’s ability to detect malicious activity quickly. This allows you to choose the format that best suits. What is the general security log. This easy to use template will help you figure out what initial steps you need to take to properly start. Get your free copy now! They play an important role. Web execute and sign your security log template with complete confidence that your document will be safeguarded and that your esignature will be legally binding and admissible in. Web downoload your free security equipment log. Web security seal log note: Web a security log form is used by security professionals to record and document security events. Log collection and analysis is critical for an enterprise’s ability to detect malicious activity quickly. Web incident response log template. Web security seal log note: Security shift report (watermarked) by 1st reporting. Web our security incident report template is provided in multiple file formats, including microsoft word, excel, and pdf. Web audit log management policy template for cis control 8. 50 printable log sheet templates [direct download] most businesses use a log sheet to keep track of chronological notes or incidents that happen in the place of. Log files are a key part of any iso 27001 compliant information security management system (isms). This allows you to choose the format that best suits. Web to fully benefit from audit logging, companies should follow best practices like defining a clear log management policy, regularly reviewing and analyzing logs,. This easy to use template will help you figure out what initial steps you need to take to properly start. Enter your name, date, shift start. The security guard daily report sample is a great way to demonstrate. What is the general security log. If applicable, the security seal log template can be used to capture tamper seal records.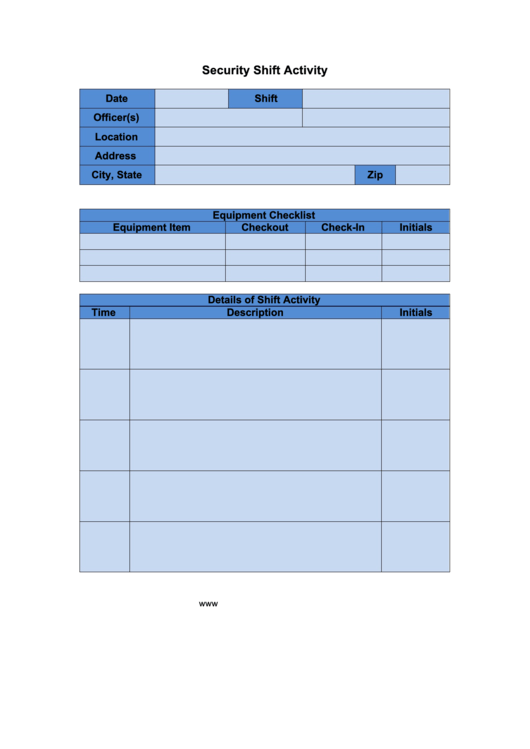
Top Security Log free to download in PDF format
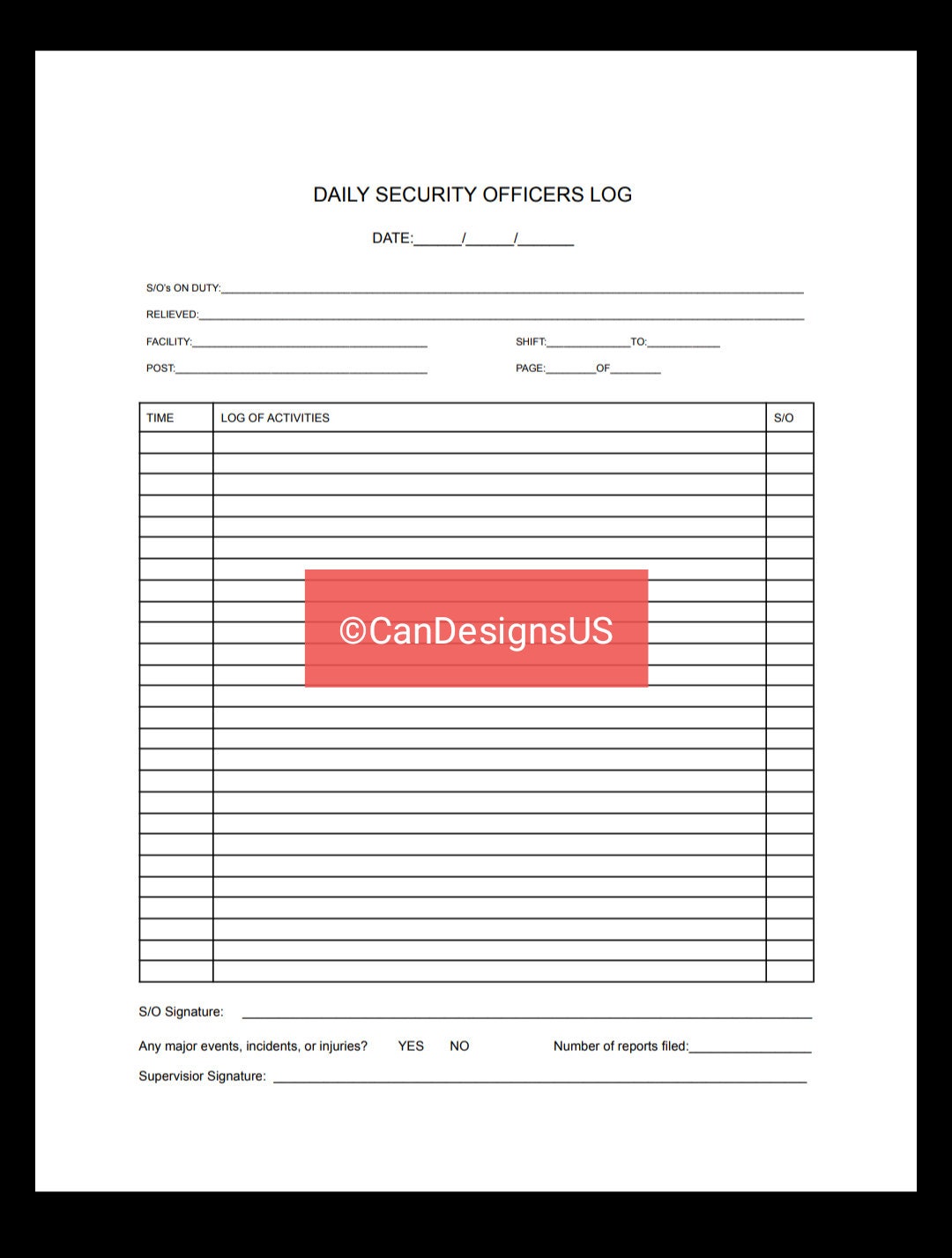
Printable Security Guard Daily Log Tracker Etsy

Security Activity Log Sheet Template jawerchecks
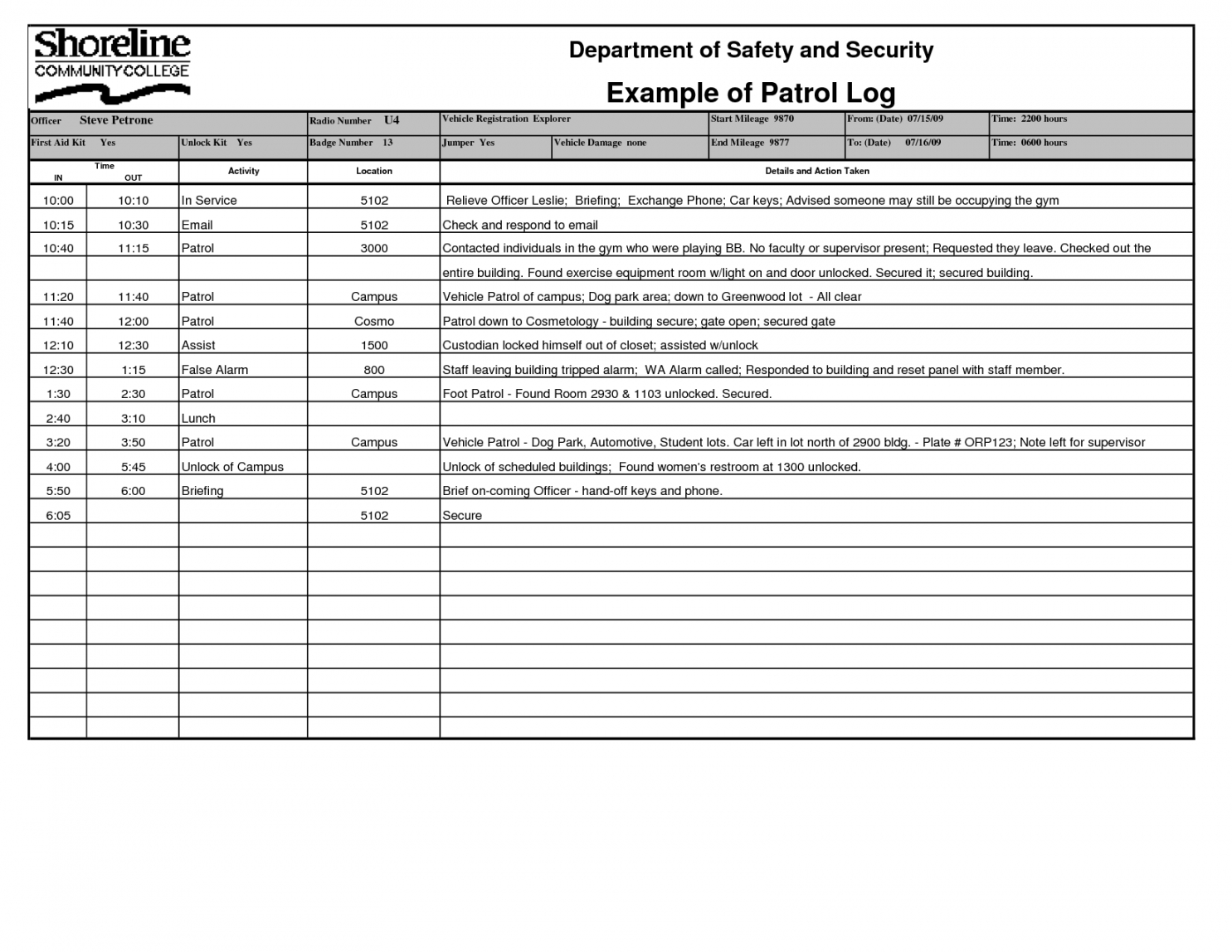
Security Patrol Checklist Template
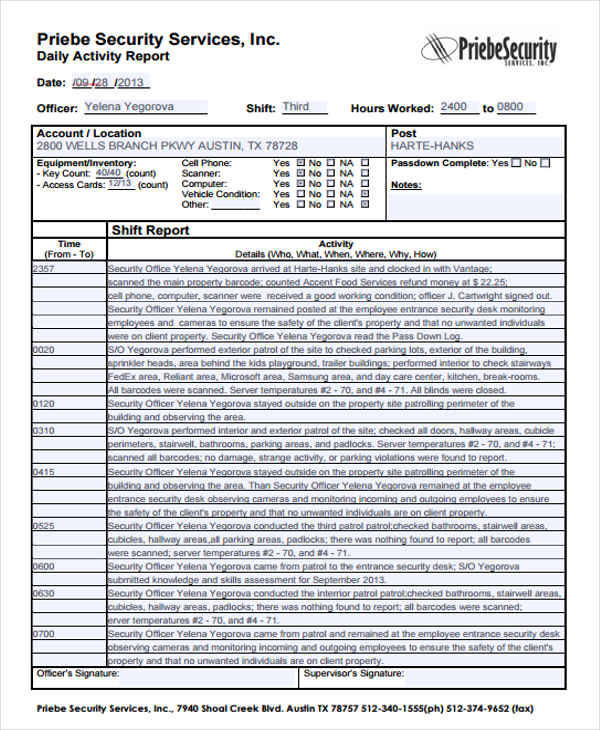
FREE 34+ Daily Log Templates in PDF MS Word
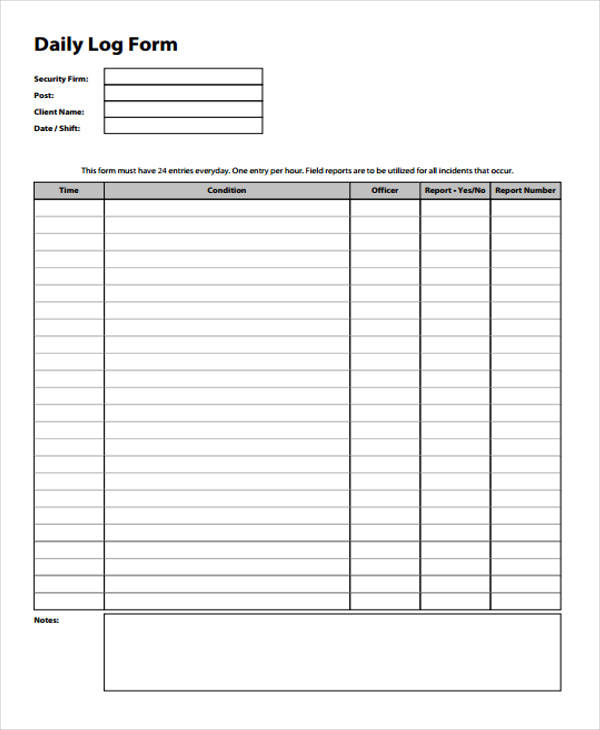
FREE 34+ Daily Log Templates in PDF MS Word
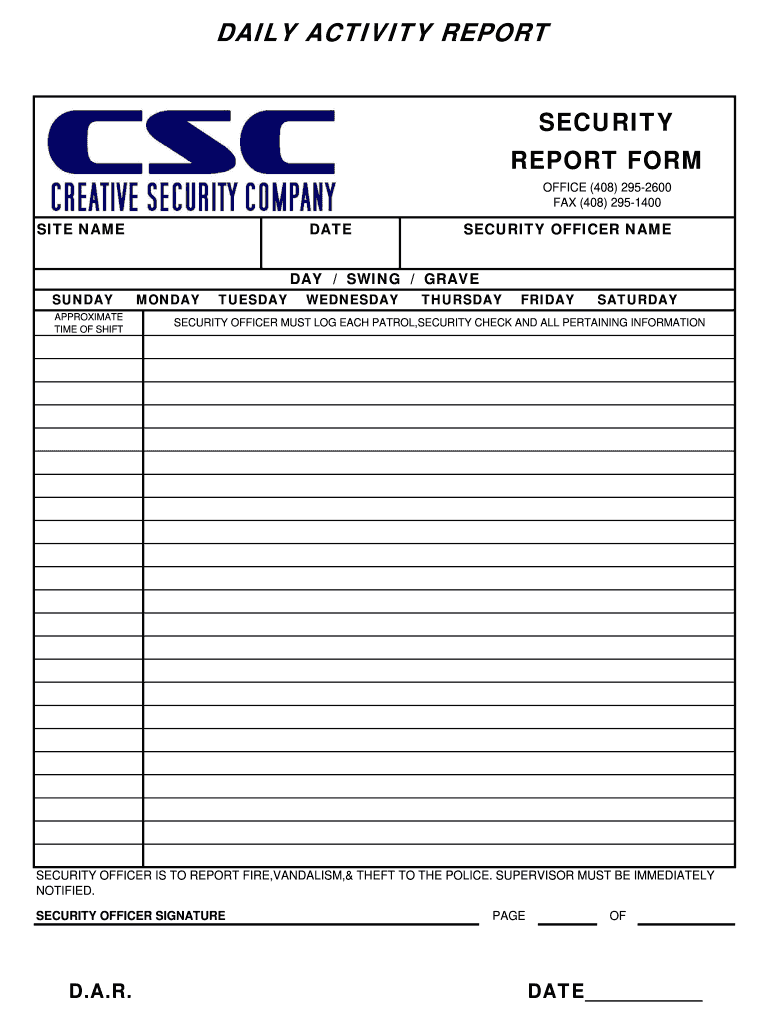
Security Guard Logbook Sample Editable template airSlate SignNow

Security Log Book Template Gráfico por allaboutkdp · Creative Fabrica
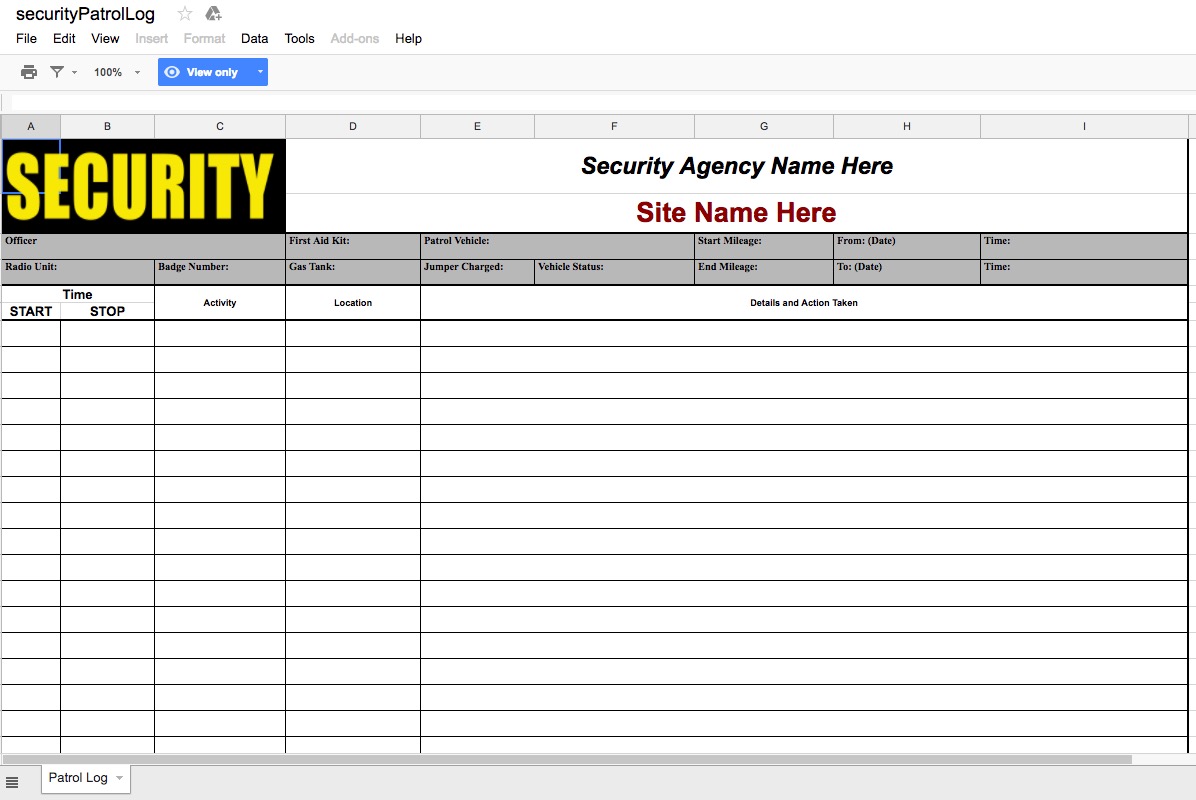
Editable Security Patrol Log Template Fill Print Download Law Forms In
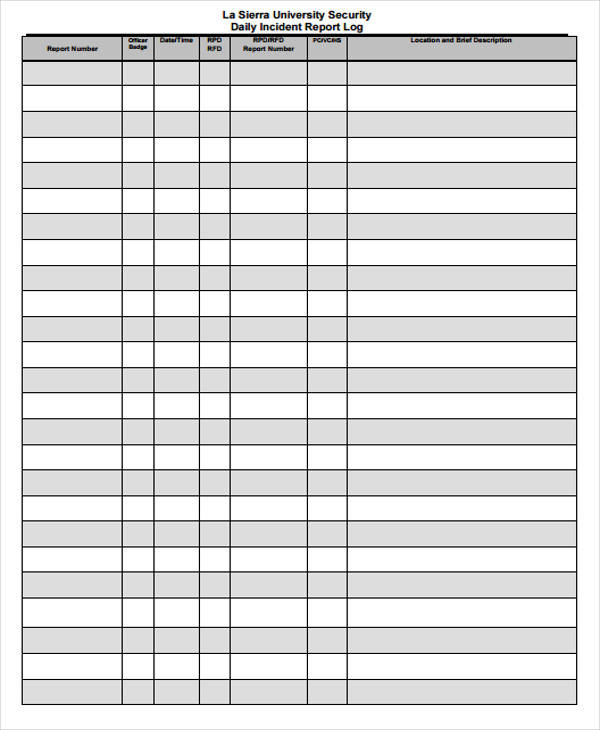
FREE 34+ Daily Log Samples & Templates in PDF MS Word
Use The Security Equipment Log To Track And Maintain Records Of Security Equipment Within A Facility Or Organization, Including.
This Free And Downloadable Incident Management Policy Template Is Vital For Organizations Seeking To Protect Against Data Breaches, Ensure.
Web An Incident Log Template In It Governance Is A Structured Document Designed To Systematically Capture And Record Details Of Security Incidents, Disruptions,.
Get Your Free Copy Now!
Related Post: